Social engineering is explained here in the context of ethical hacking (penetration testing) based on a uOttawa PhD thesis (2020) completed at the School of Electrical Engineering and Computer Science (EECS), Faculty of Engineering, on the topic of ethical hacking sociotechnology titled Technoethics and sensemaking: Risk assessment and knowledge management of ethical hacking in a sociotechnical society (thesis advisory committee: uOttawa professors Rocci Luppicini, Liam Peyton, and Andre Vellino).
- What is social engineering?
- Social engineering in penetration testing
- The four most common types of social engineering attacks
You may also be interested in OSINT analyst competency areas.
What is social engineering?
In its National Cyber Threat Assessment 2018 report, Canada’s Communications Security Establishment (CSE) identifies 1) Data Breaches – from commercial espionage, commercial data theft, and social engineering – and 2) Exploiting Trusted Relationships as two key cybersecurity threat areas to businesses.
Social engineering can be understood as a cybersecurity threat to the confidentiality, integrity, and availability of business data assets. The top higher education information security risks in Canada and the U.S. that were a priority for IT in 2016 were phishing and social engineering, followed by end-user awareness, and training, and education (Grama & Vogel, 2017).
Social engineering plays into human nature’s inclination to trust. Social engineering tactics involve manipulating a person in order to access corporate systems and private information.
Social engineering in penetration testing
Social engineering can be situated within a risk-based information security risk management framework – more specifically, within ethical hacking or penetration testing as an information security risk assessment method.
Understanding the security risk to an information asset involves first identifying threats and threat sources to the confidentiality, integrity, and availability of said asset – from accidental fires and natural disasters to information theft by malicious hackers and asset sabotage by business and political adversaries. This involves assigning a threat level to each identified threat based on the likelihood of it occurring and the estimated impact/cost. Next is understanding and assessing (prioritizing) systemic vulnerabilities that threat actors can exploit to compromise or damage the information asset.
Automated vulnerability scanning tools are used by penetration testers to identify software and network vulnerabilities. Physical vulnerabilities may also need to be enumerated. Systemic vulnerabilities also include a lack of security awareness among employees and technology users, including contractors and suppliers, leaving them susceptible to social engineering-based attacks.
The first phase of ethical hacking or penetration testing involves extensive intelligence gathering. Open source information on the Internet and from other public sources can be used to build a profile of the target user or system to determine entry points into a computer system. For NIST (2008), the discovery phase of the penetration testing process spans OSINT (open source intelligence) or recon (reconnaissance) or footprinting, network enumeration, and port scanning.
OSINT is one of several primary intelligence disciplines that include (Rosenbach, Peritz, & LeBeau, 2009, pp. 12-13):
⦁ SIGINT, or Signals Intelligence, which involves the interception of COMINT (Communications Intelligence) and ELINT (Electronic Intelligence).
⦁ HUMINT, or Human Intelligence, which is gathered from human sources, typically through clandestine operations.
⦁ GEOINT, or Geospatial Intelligence, which is based on the visual representation of activities on Earth.
⦁ MASINT, or Measurement and Signatures Intelligence, obtained by analyzing data such as missile plume signatures and uranium particles in the air.
Depending on the testing goals put forth in the planning phase, social engineering activity can be considered part of the initial intelligence gathering phase, i.e., part of OSINT, or it can be considered a type of penetration testing in its own right, as we would consider network penetration testing and exploitation, website and wireless network penetration testing, physical penetration testing, and cloud penetration testing as types of penetration testing.
During OSINT, the penetration tester uncovers possible weaknesses and entry points within the security posture of the target organization, including the network, applications, website and wireless networks, physical facilities, cloud-based systems, employees, and more. The vast majority of OSINT activity is passive in nature. Passive reconnaissance involves gathering information from the public domain in places like Internet registries, Google, newspapers, and public records. At this stage “the target does not even know generally that they are the subject of surveillance” (Walker, 2017, p. 44). Active reconnaissance includes social engineering and any tactic “that requires the hacker to interact with the organization” (Walker, 2017, p. 45).
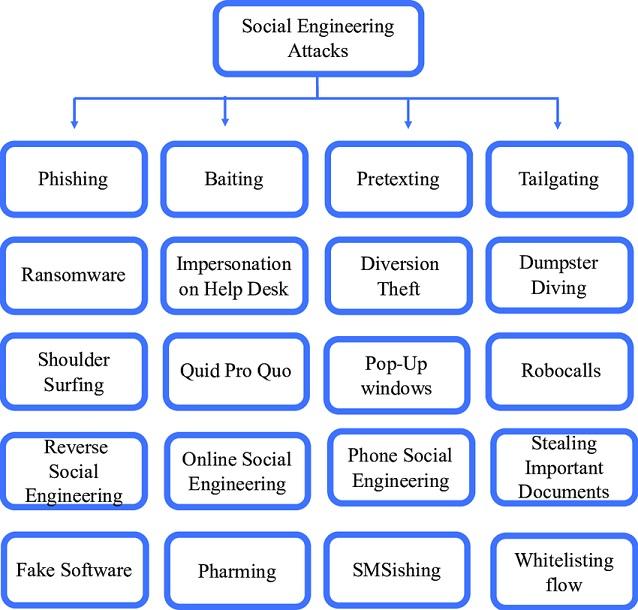
The four most common types of social engineering attacks
1. Phishing: is the leading tactic leveraged by today’s ransomware hackers, typically delivered in the form of an email, chat, web ad or website designed to impersonate a real system and organization. Often crafted to deliver a sense of urgency and importance, the message within these emails often appears to be from the government or a major corporation and can include logos and branding.
Whaling refers to spear-phishing aimed specifically at senior executives or other high-profile recipients with privileged access to company resources. Cyber threat actors are increasingly using the whaling social engineering tactic against businesses. Whaling occurs when an executive with authority to issue large payments receives a message appearing to come from a relevant department or employee, urging them to direct funds to an account controlled by a cyber threat actor. This type of social engineering can lead to major financial losses and reputational damage. Like other social engineering techniques, whaling is designed to exploit predictable human behaviour (CSE, 2018, p. 17).
2. Baiting: similar to phishing, baiting involves offering something enticing to an end user in exchange for private data. The “bait” comes in many forms, both digital, such as a music or movie download, and physical, such as a branded flash drive labeled “Executive Salary Summary Q3 2016” that is left out on a desk for an end user to find. Once the bait is taken, malicious software is delivered directly into the victim’s computer.
Quid Pro Quo: similar to baiting, quid pro quo involves a request for the exchange of private data but for a service. For example, an employee might receive a phone call from the hacker posed as a technology expert offering free IT assistance in exchange for login credentials.
3. Pretexting: is when a hacker creates a false sense of trust between themselves and the end user by impersonating a co-worker or a figure of authority within the company in order to gain access to private data. For example, a hacker may send an email or a chat message posing as the head of IT Support who needs private data in order to comply with a corporate audit (that isn’t real).
4. Tailgating: is when an unauthorized person physically follows an employee into a restricted corporate area or system. The most common example of this is when a hacker calls out to an employee to hold a door open for them as they’ve forgotten their RFID card. Another example of tailgating is when a hacker asks an employee to “borrow” a private laptop for a few minutes, during which the criminal is able to quickly steal data or install malicious software.
Related content
Critical thinking theory, teaching, and practice
Ethical Hacking Sociotechnology
Karl Weick – sensemaking through organizing
OSINT analyst competency areas
WordPress security best practices
Back to DTI Courses
Other content
1st Annual University of Ottawa Supervisor Bullying ESG Business Risk Assessment Briefing
Disgraced uOttawa President Jacques Frémont ignores bullying problem
How to end supervisor bullying at uOttawa
PhD in DTI uOttawa program review
Rocci Luppicini – Supervisor bullying at uOttawa case updates
The case for policy reform: Tyranny
The trouble with uOttawa Prof. A. Vellino
The ugly truth about uOttawa Prof. Liam Peyton
uOttawa engineering supervisor bullying scandal
uOttawa President Jacques Frémont ignores university bullying problem
uOttawa Prof. Liam Peyton denies academic support to postdoc
Updated uOttawa policies and regulations: A power grab
What you must know about uOttawa Prof. Rocci Luppicini
Why a PhD from uOttawa may not be worth the paper it’s printed on
Why uOttawa Prof. Andre Vellino refused academic support to postdoc



