We continue our studies of the topics in the Security Fundamentals section of the CCNA exam blueprint. This lesson covers dynamic ARP inspection configuration and verification on Cisco switches. Dynamic ARP Inspection (DAI) is covered in exam topic 5.7, which says you must be able to “Configure Layer 2 security features (DHCP snooping, dynamic ARP inspection, and port security)”. We have already covered switch port security configuration and verification as well as DHCP snooping configuration and verification. It is time to study dynamic ARP inspection configuration and verification.
This lesson first reviews some important ARP details for a refresher of how ARP normally works. Then we explore gratuitous ARP as an attack vector for a man in the middle attack. DAI logic is then discussed to help us understand how DAI can guard against this sort of attack. Finally, dynamic ARP inspection (DAI) configuration and verification are explained for required and optional features. This post constitutes Issue 40 of my CCNA 200-301 study notes.
- Introduction to dynamic ARP inspection (DAI)
- Gratuitous ARP as an attack vector
- Dynamic ARP inspection logic
- Dynamic ARP inspection configuration
- Limiting DAI message rates
- Configuring optional DAI message checks
- IP ARP inspection configuration summary
- Command review
- Practice quiz questions
- Key references
You may also be interested in CCNA 200-301 study notes.
Introduction to dynamic ARP inspection (DAI)
DAI feature on a switch inspects incoming ARP messages on untrusted ports to filter those it deems to be part of an attack. DAI’s core feature cross references incoming ARP messages with information in the DHCP snooping binding table and any configured ARP ACLs. If an incoming ARP message does not match the tables in the switch, the switch discards the ARP message.
To understand the attacks DAI can prevent, first we need to compare normal ARP operations with the abnormal use of ARP applied in some types of attacks. First we review some important ARP details, then we look at how an attacker can send an ARP reply, called a gratuitous ARP, tricking hosts into adding incorrect ARP entries to their ARP tables.
Figure 8-9 shows a typical sequence in normal IP ARP. PC1 needs to send an IP packet to its default router R2, so PC1 first sends an ARP request message to learn R2’s MAC address. R2 sends back an ARP reply, listing R2’s MAC address. The ARP request message goes something like this: host 172.16.2.2 send me your MAC. My IP and MAC are so and so. Please and thank you.
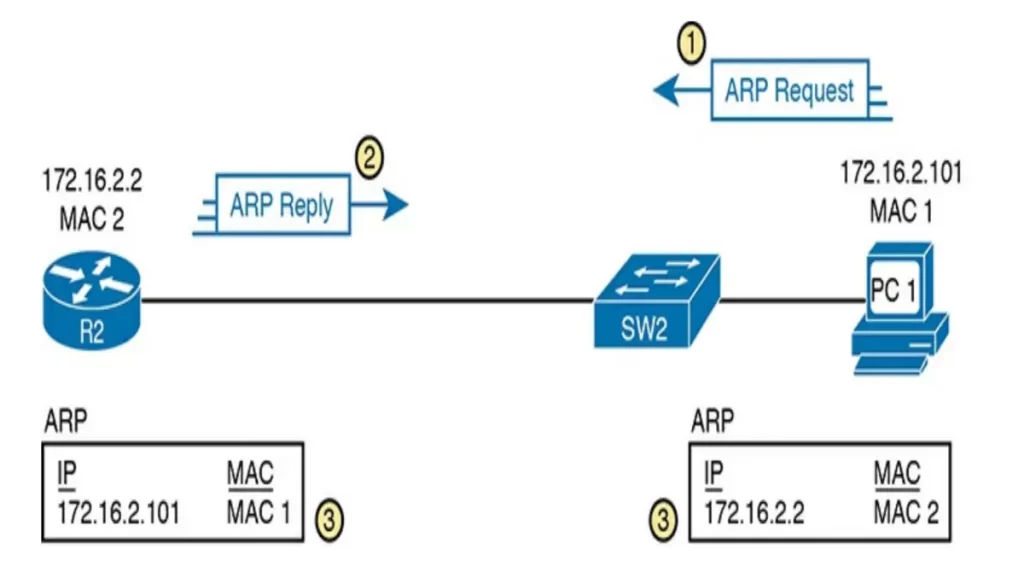
In more details:
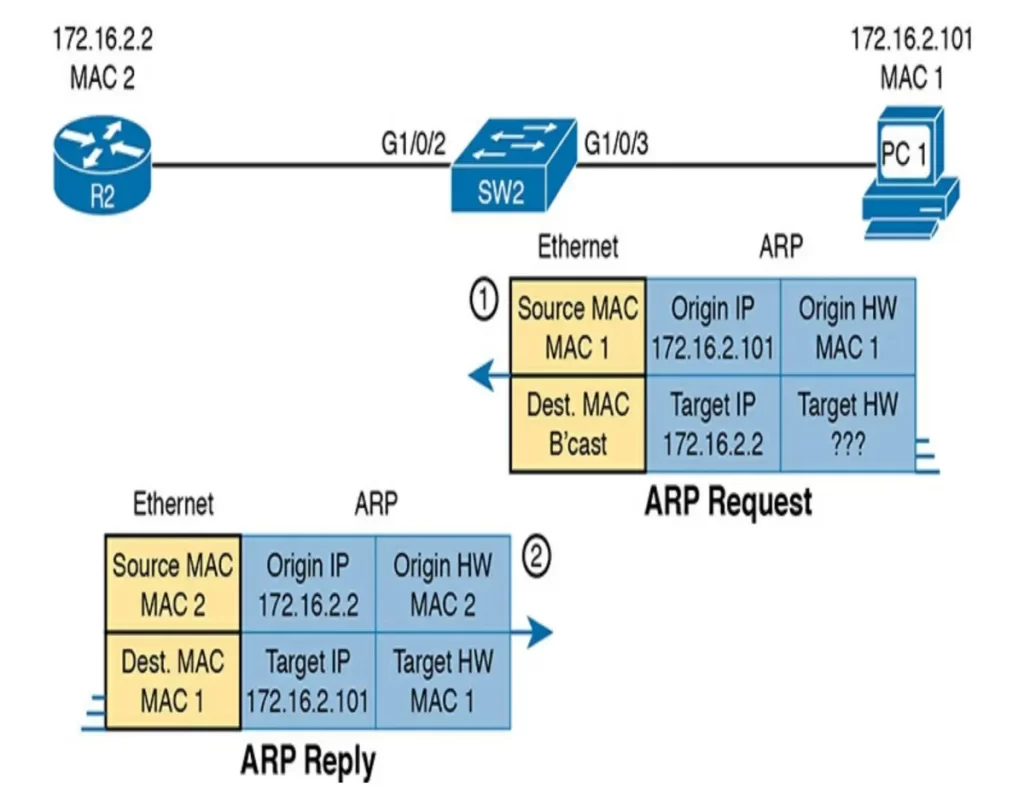
Gratuitous ARP as an attack vector
ARP supports the idea of a gratuitous ARP message with these features:
- It is an ARP reply.
- It is sent without having first received an ARP request.
- It is sent to an Ethernet destination broadcast address so that all hosts in the subnet receive the message.
Gratuitous ARPs represent a vulnerability because they let a sending host make other hosts change their ARP tables. Attackers can exploit this vulnerability. In Figure 8-11, an attacker, PC A, initiates a gratuitous ARP using PC1’s IP address and PC A’s MAC address. This causes the router to update its ARP table.
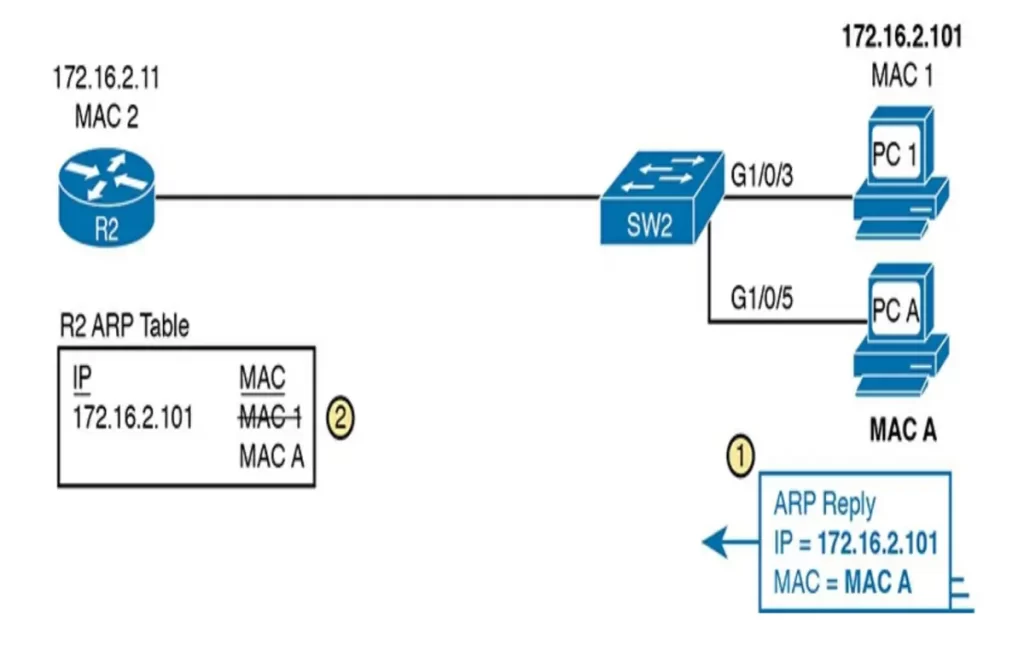
Now when R2 forwards IP packets to PC1’s IP address (172.16.2.101), R2 will encapsulate them in an Ethernet frame with PC A as the destination. PC A can thus copy all packets destined to PC1. This could be part of a man in the middle attack: after PC A copies a packet, PC A forwards the packet inside a new frame to PC1 so that PC1 still works.
Dynamic ARP inspection logic
Several DAI features can prevent this kind of attack.
DAI implements the same general rules concerning trusted and untrusted ports as DHCP snooping.
Access ports connected to end-user devices are often untrusted by both DHCP Snooping and DAI. Ports connected to other switches, routers, the DHCP server—anything other than links to end-user devices—should be trusted by DAI. (Odom, 2020, p. 432)
For untrusted interfaces, DAI confirms an ARP’s correctness based on DHCP snooping’s data about the earlier DHCP messages. Normal DHCP messages list the IP address leased to a host as well as that host’s MAC address. The DHCP snooping feature also records those facts into the switch’s DHCP snooping binding table.
For any DAI untrusted ports, DAI compares the ARP message’s origin IP and origin MAC address fields to the DHCP Snooping binding table. If found in the table, DAI allows the ARP through, but if not, DAI discards the ARP. (Odom, 2020, p. 431)
Figure 8-13 shows the first step in which the attacker at PC A attempts the gratuitous ARP shown in Figure 8-11. At step 2, DAI cross references the information in the ARP message received from PC A containing PC A’s IP and MAC addresses to the information in the DHCP snooping binding table. Not finding a match, DAI discards the message.
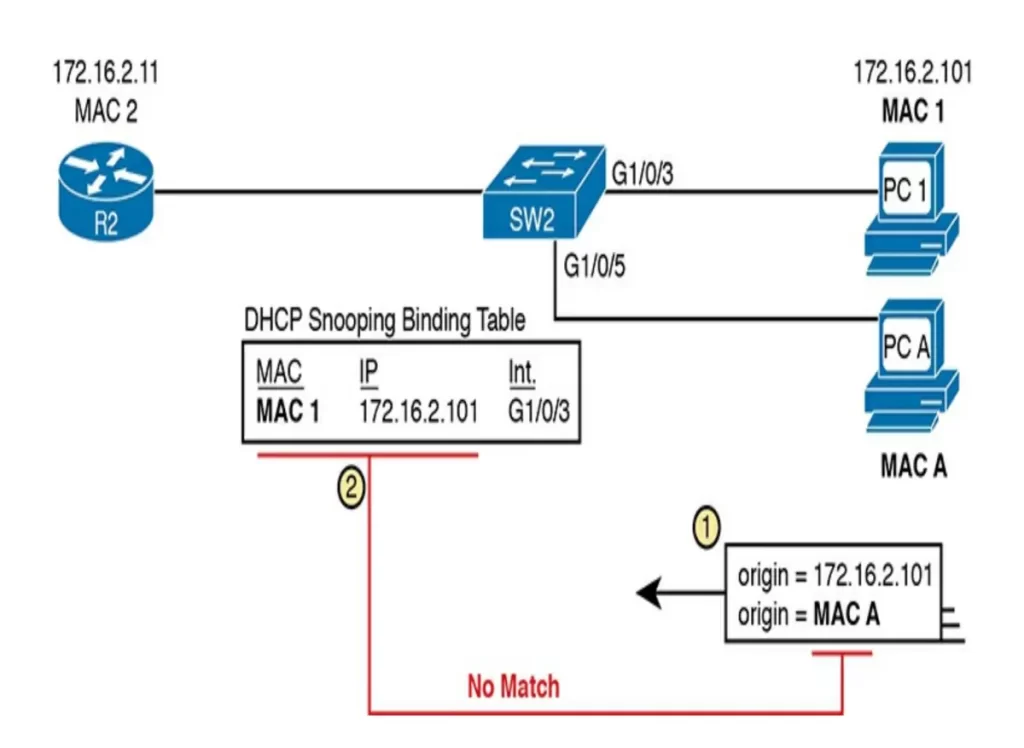
Beside the DHCP snooping binding table, DAI can use similar statically configured data that lists correct pairs of IP and MAC addresses via a tool called ARP ACLs. Using ARP ACLs with DAI is useful for ports connected to devices that use static IP addresses rather than DHCP. DAI looks for both the DCHP snooping binding data and ARP ACLs.
DAI can optionally perform other checks beyond that core feature. For example, does the Ethernet header that encapsulates the ARP have addresses that match the ARP origin and target MAC addresses?
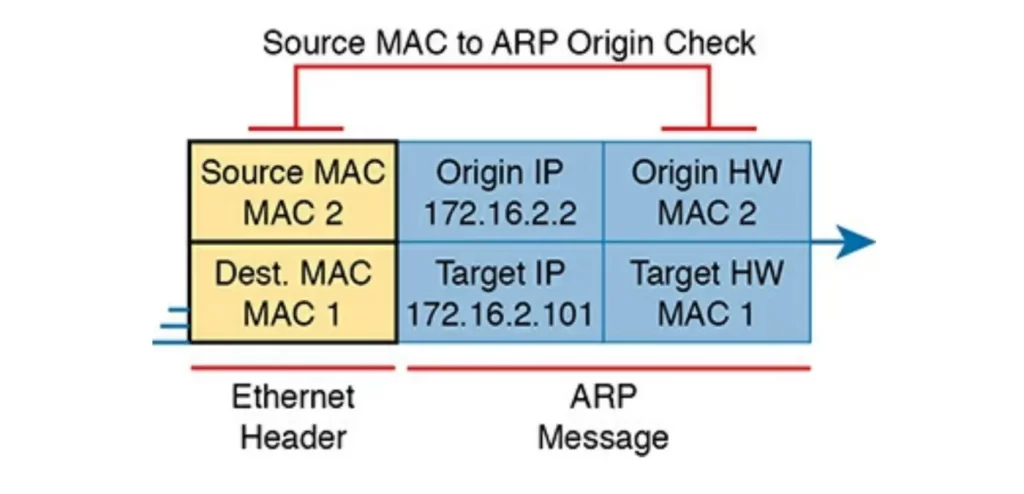
DAI can be enabled to make the comparisons shown in Figure 8-14, discarding:
- Messages with an Ethernet header source MAC address that is not equal to the ARP origin hardware (MAC) address.
- ARP reply messages with an Ethernet header destination MAC address that is not equal to the ARP target hardware (MAC) address.
- Messages with unexpected IP addresses in the two ARP IP address fields.
Note that DAI itself can be susceptible to DoS attacks because DAI, like DHCP snooping, does its work in the switch CPU rather than in the switch ASIC. An attacker can drive up CPU usage in the switch by generating large numbers of ARP messages to overwhelm the CPU. One remedy is rate limiting the number of ARP messages on a port over time.
Dynamic ARP inspection configuration
First we look at DAI configuration with mostly default settings and with reliance on DHCP snooping. Then we look at configuring DAI with optional features – rate limits, automatic recovery from err-disabled state, and how to enable additional checks of incoming ARP messages.
Before configuring DAI, you need to make a few decisions based on your goals, topology, and device roles:
- Rely on DHCP snooping, ARP ACLs, or both.
- If using DHCP snooping, make the correct ports trusted for DHCP snooping.
- Choose the VLAN(s) on which to enable DAI.
- Make DAI trusted (the default setting is untrusted) on select ports in those VLANs, typically for the same ports you trusted for DHCP snooping.
We will use the sample network in Figure 8-15 for our configuration examples – the same network topology (Figure 8-8) used in the DHCP snooping configuration topic.
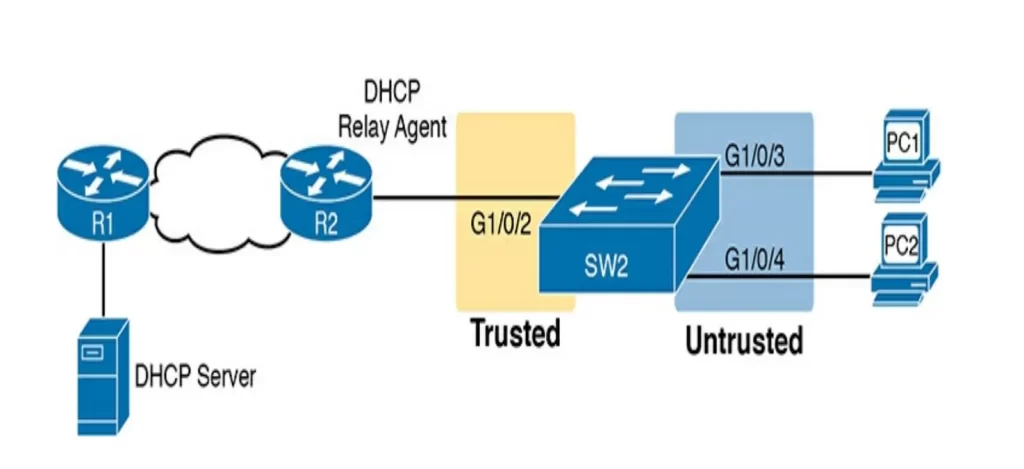
As with DHCP snooping, SW2 should be configured to trust the port connected to the router (G1/0/2) but not to trust the two ports connected to the PCs (the bad guys typically use end host devices, such as PCs, not routers or switches, to infiltrate the network).
Example 8-5 shows how to enable DAI on SW2 in Figure 8-15—a configuration that follows a similar progression compared to DHCP snooping. All ports connect to VLAN 11. To enable DAI in VLAN 11, use the ip arp inspection vlan 11 command from global config mode. Then add the ip arp inspection trust interface subcommand to change the logic on port G1/0/2 (connected to R2) to be trusted by DAI,
Example 8-5 IP ARP Inspection Configuration to Match Figure 8-15:
SW2(config)#ip arp inspection vlan 11
SW2(config)#interface g1/0/2
SW2(config-if)#ip arp inspection trust
Example 8-5 enables DAI on SW2 but the configuration omits both DHCP snooping and ARP ACLs. If we configure SW2 only with the commands shown in Example 8-5, the switch would filter all ARPs entering all untrusted ports in VLAN 11.
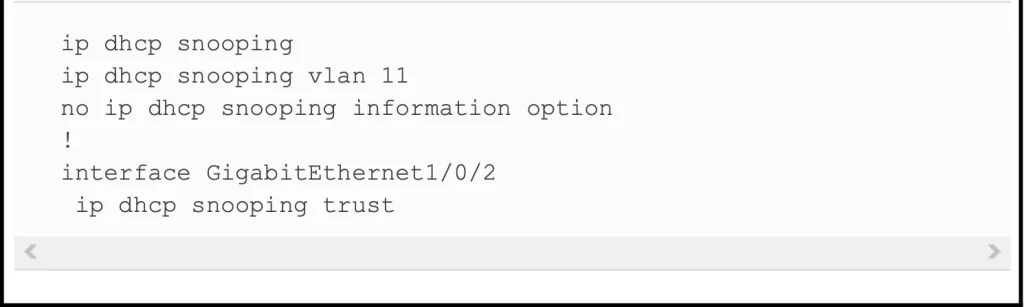
Example 8-6 shows a complete and working DAI configuration wherein the DHCP snooping configuration was added to match the DAI configuration in Example 8-5. Example 8-6 combines Example 8-1’s DHCP snooping configuration for this same topology to the DAI configuration in Example 8-5. DAI-specific configuration lines are highlighted in Example 8-6.
Example 8-1 DHCP Snooping Configuration to Match Figure 8-8 / Figure 8-15 (Odom, 2020)
Example 8-6 IP DHCP Snooping Configuration Added to Support DAI (Odom, 2020)
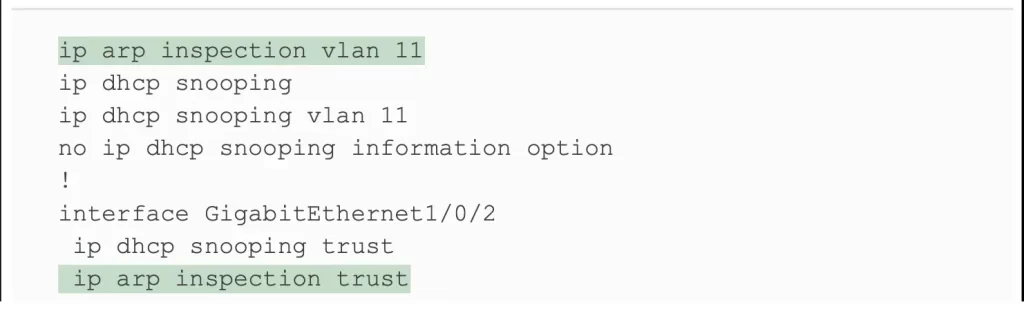
With the configuration in Example 8-6, the switch’s DHCP snooping feature gathers information from the incoming DHCP messages and combines it with information about the port (e.g., G1/0/3) to build the DHCP snooping binding table (e.g., traffic entering SW2’s G1/0/3 interface is associated with the IP address and the MAC address of PC1). Next, any incoming ARP messages on DAI untrusted ports must match the information in that binding table.
Let’s confirm the configurations, based on the configuration in Example 8-6.
The show ip arp inspection command gives configuration settings along with status variables and counters. See Example 8-7. The highlighted lines show the total ARP messages received on untrusted ports in VLAN 11 and the number of discarded ARP messages (currently 0).
Example 8-7 SW2 IP ARP Inspection Status (Odom, 2020)
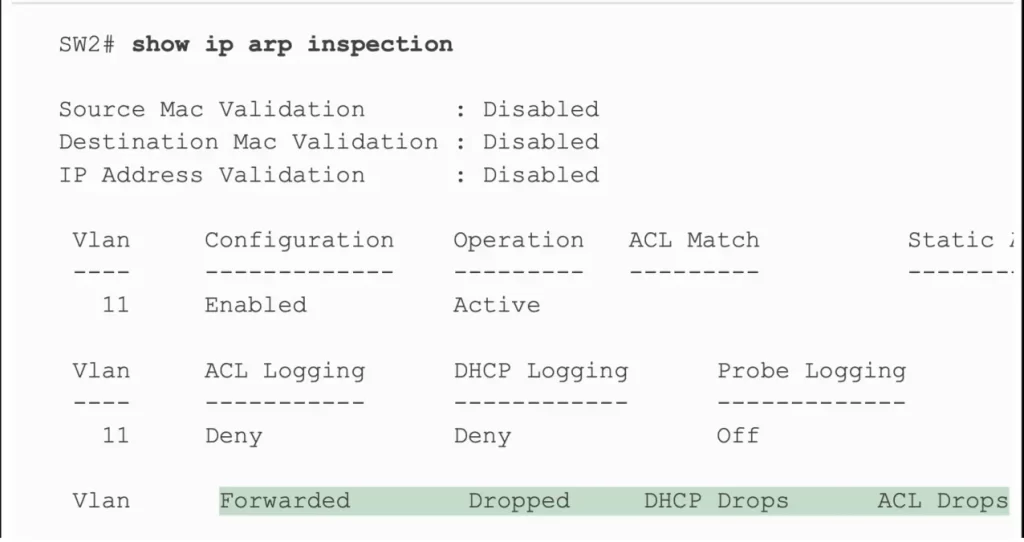
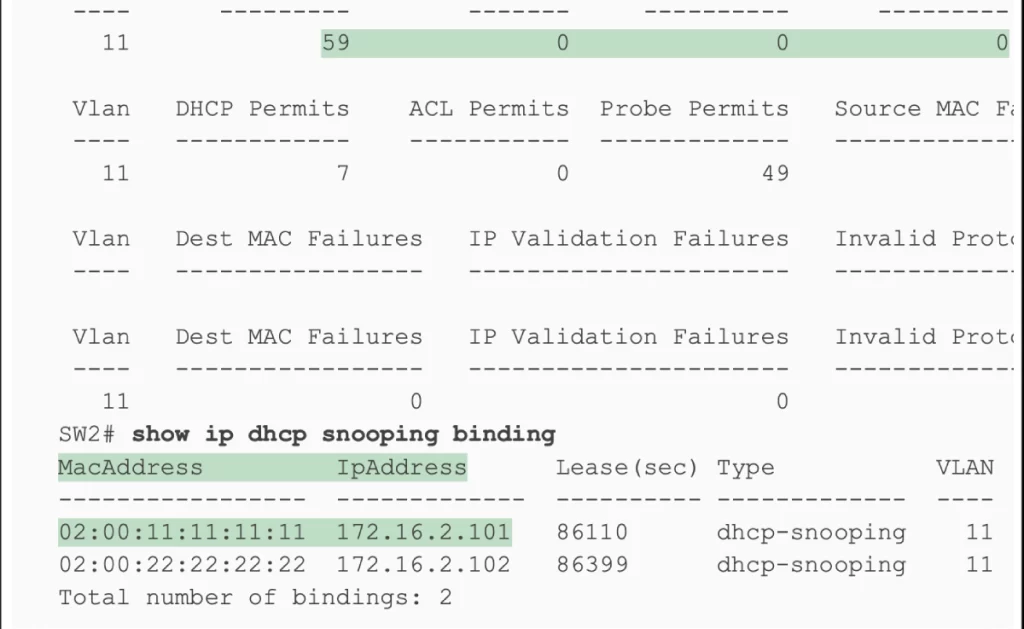
Note the output for the show ip dhcp snooping binding command on switch SW2. The first two columns list a MAC and IP address learned from the DHCP messages. If an ARP message arrives at SW2 from PC1, a message listing PC1’s MAC address (0200.1111.1111) and IP address (172.16.2.101) as the origin MAC and IP addresses, per this output, the switch would find that matching data and allow the ARP message.
What if SW2 receives an invalid ARP message on port G1/0/4 in Figure 8-15? Let’s look at Example 8-8 which shows some details of what happens then.
An invalid ARP message was created by configuring PC2 with a static IP address of 172.16.2.101 (PC1’s DHCP-leased IP address). PC2’s claimed origin MAC and IP addresses in the ARP message are shown in the highlights in the log message at the top of the example. Looking back at the bottom of Example 8-7, these two addresses do not exist in the DHCP snooping binding table, so DAI rejects the ARP message.
Example 8-8 Sample Results from an ARP Attack (Odom, 2020)
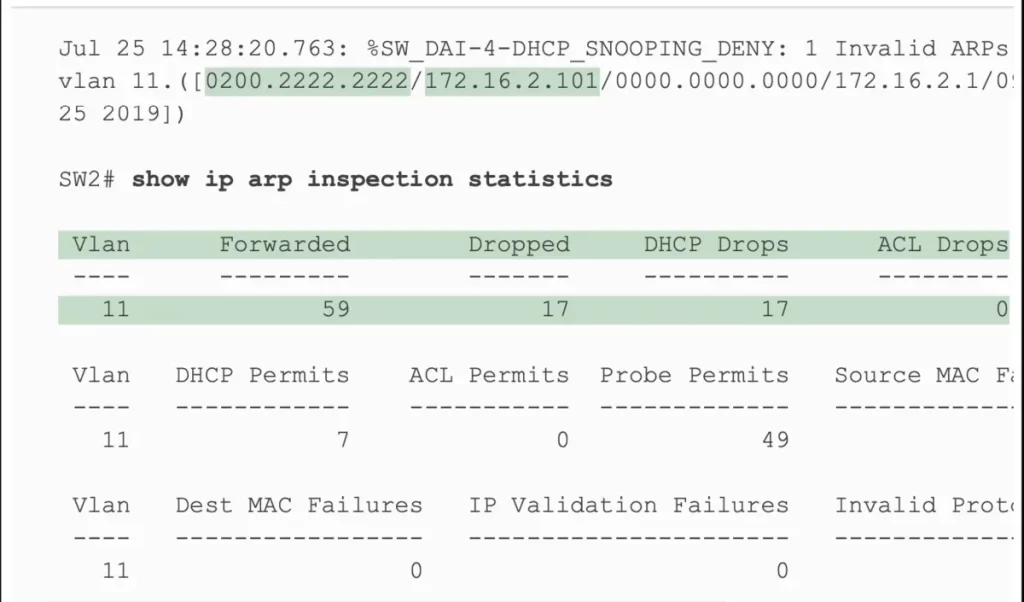
The statistics from the show ip arp inspection statistics command also confirm that SW2 has dropped some ARP messages. The output shows 17 total dropped ARP messages in VLAN 11. That same highlighted line confirms that it dropped all 17 because of the DHCP snooping binding table (“DHCP Drops”). Zero ARP messages were dropped due to an ARP ACL (“ACL Drops”).
Limiting DAI message rates
DAI can be the target of a DoS attack with the attacker generating a large number of ARP messages. Like DHCP snooping, which can also be the target of a DoS attack, “DAI supports the configuration of rate limits to help prevent those attacks, with a reaction to place the port in an err-disabled state, and with the ability to configure automatic recovery from that err-disabled state” (Odom, 2020, p. 440).
But the DHCP snooping and DAI rate limits have some differences in operation, defaults, and in configuration:
- DAI defaults to use rate limits for all interfaces (trusted and untrusted), while DHCP snooping defaults to not use rate limits.
- DAI allows the configuration of a burst interval (a number of seconds) with a rate limit logic such as “x ARP messages over y seconds”, while DHCP snooping does not define a burst setting.
Example 8-9 shows both DAI and DHCP snooping rate limit configuration together.
Example 8-9 repeats the exact same DHCP snooping commands in Example 8-3 but adds the DAI configuration (highlighted).
Example 8-3 Configuring DHCP Snooping Message Rate Limits (Odom, 2020)
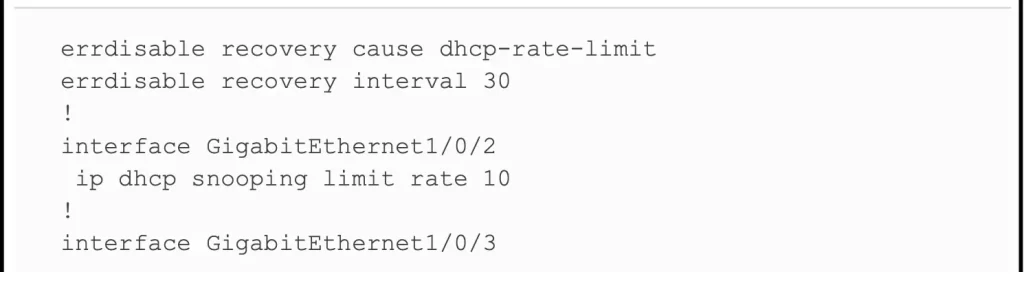
Example 8-9 Configuring ARP Inspection Message Rate Limits (Odom, 2020)
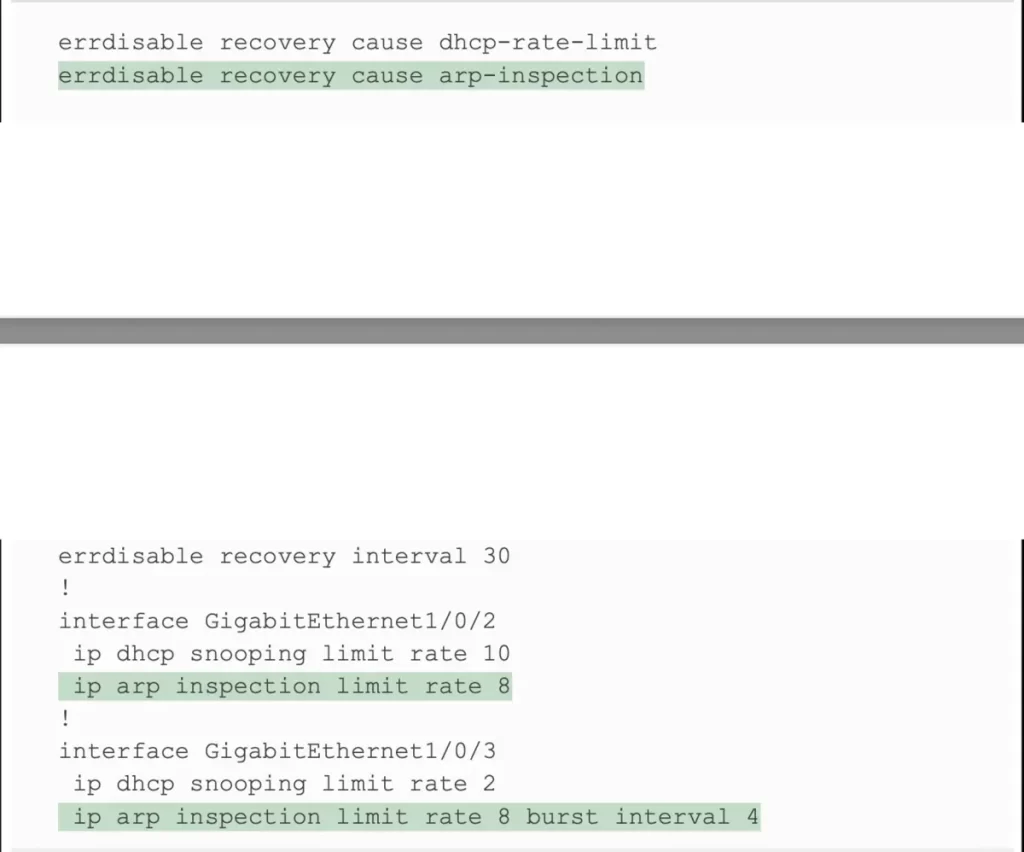
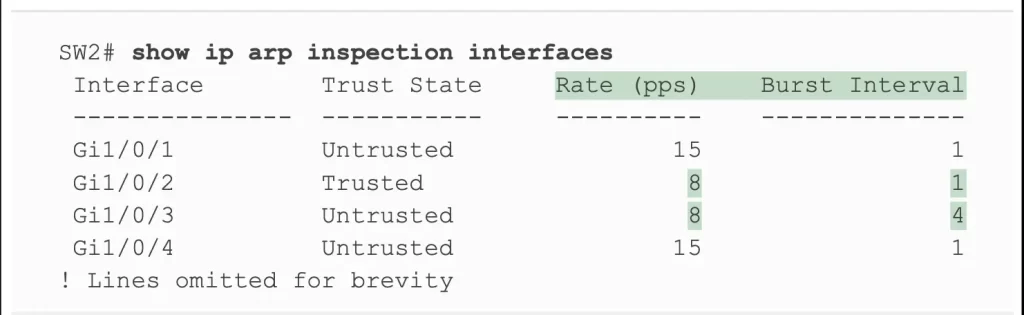
The output entries in Example 8-10 confirm the configuration settings. Port G1/0/2 in Example 8-9 is configured with a rate of 8 messages for each (default) burst of 1 second, and port G1/0/2 in Example 8-10 also lists a rate of 8 and burst interval of 1. Similarly, port G1/0/3 in Example 8-9 is configured with a rate of 8 over a burst of 4 seconds, with Example 8-10 confirming those same values for port G1/0/3. Interfaces G1/0/1 and G1/0/4 show the default settings of a rate of 15 messages over a one-second burst.
Example 8-10 Confirming ARP Inspection Rate Limits (Odom, 2020)
Configuring optional DAI message checks
For DAI untrusted ports, DAI compares the ARP message’s origin IP and origin MAC address fields to the DHCP snooping binding table in the switch (if found in the table, DAI allows the ARP through, but if not, DAI discards the ARP). DAI can also perform other checks. Those checks require more CPU, but they also help prevent other types of attacks.
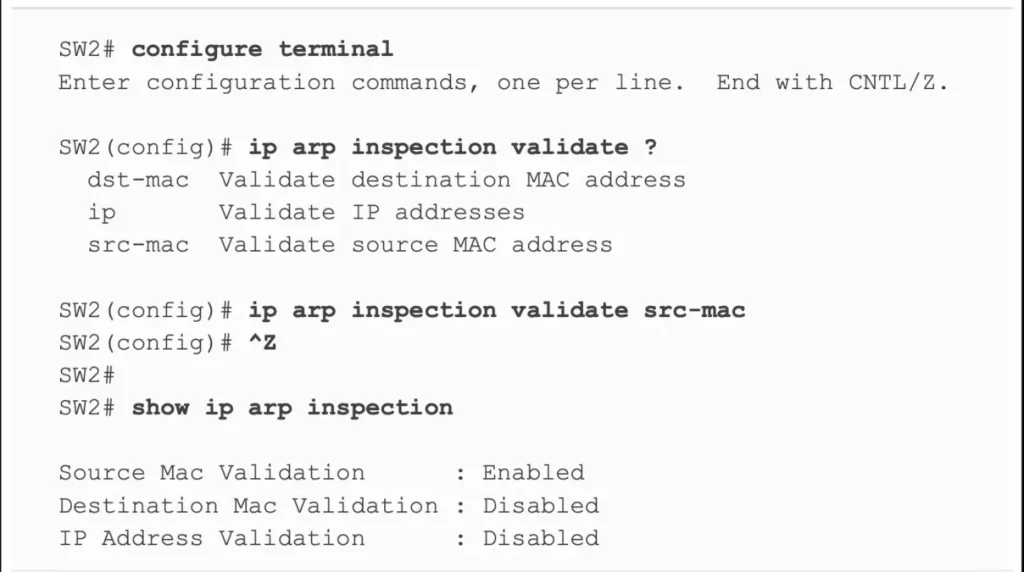
Example 8-11 shows how to configure three additional checks. You can configure one, two, or all three options. When configuring optional DAI validation checks, to configure multiple checks you should configure them all in a single command, otherwise only the last command entered will take effect. Example 8-11 shows the three options, with the src-mac (source mac) option configured.
Example 8-11 Confirming ARP Inspection Rate Limits (Odom, 2020)
IP ARP inspection configuration summary
Here’s a summary of the configuration commands and steps to configure Dynamic IP ARP inspection (Odom, 2020, pp. 443-444):
- Step 1. Use the ip arp inspection vlan vlan-list global command to enable Dynamic ARP Inspection (DAI) on the switch for the specified VLANs.
- Step 2. Separate from the DAI configuration, also configure DHCP Snooping and/or ARP ACLs for use by DAI.
- Step 3. Configure the ip arp inspection trust interface subcommand to override the default setting of not trusted.
- Step 4. (Optional): Configure DAI rate limits and err-disabled recovery:
- Step 4.1. (Optional): Configure the ip arp inspection limit rate number [burst interval seconds] interface subcommand to set a limit of ARP messages per second, or ARP messages for each configured interval.
- Step 4.2. (Optional): Configure the ip arp inspection limit rate none interface subcommand to disable rate limits.
- Step 4.3. (Optional): Configure the errdisable recovery cause arp-inspection global command to enable the feature of automatic recovery from err-disabled mode, assuming the switch placed the port in err-disabled state because of exceeding DAI rate limits.
- Step 4.4. (Optional): Configure the errdisable recovery interval seconds global commands to set the time to wait before recovering from an interface err-disabled state (regardless of the cause of the err-disabled state).
- Step 5. (Optional): Configure the ip arp inspection validate {[dst-mac] [src-mac] [ip]} global command to add DAI validation steps.
Command review
1. Configuration commands (with examples)
1.1. First we look at DAI configuration with mostly default settings and with reliance on DHCP snooping.
SW2(config)#ip arp inspection vlan 11
→to enable DAI on the switch in VLAN 11
SW2(config)#interface g1/0/2
SW2(config-if)#ip arp inspection trust
→to change the logic on port G1/0/2 (connected to R2 in our example, Figure 8-15) in vlan 11 to be trusted by DAI (the default setting is untrusted)
Example 8-6 IP DHCP Snooping Configuration Added to Support DAI (Odom, 2020)

1.2. Next we look at configuring DAI with optional features – rate limits, automatic recovery from err-disabled state, and how to enable additional checks of incoming ARP messages.
*Configure DAI rate limits (limiting DAI message rates)
- DAI defaults to use rate limits for all interfaces (trusted and untrusted), while DHCP snooping defaults to not use rate limits.
- DAI allows the configuration of a burst interval (a number of seconds) with a rate limit logic such as “x ARP messages over y seconds”, while DHCP snooping does not define a burst setting.
- Typical default ARP inspection rate limits on Cisco switches: 15 messages over a one-second burst.
ip arp inspection limit rate number [burst interval seconds]
→interface subcommand to set a limit of ARP messages per second, or ARP messages for each configured interval
ip arp inspection limit rate none
→interface subcommand to disable rate limits
*Configure DAI err-disabled recovery
Configure the errdisable recovery cause arp-inspection global command to enable the feature of automatic recovery from err-disabled mode, assuming the switch placed the port in err-disabled state because of exceeding DAI rate limits.
Configure the errdisable recovery interval seconds global commands to set the time to wait before recovering from an interface err-disabled state (regardless of the cause of the err-disabled state).
Example 8-9 shows both DAI and DHCP snooping rate limit configuration together. The DAI configuration is italicized.
err-disable recovery cause dhcp-rate-limit
err-disable recovery cause arp-inspection
err-disable recovery interval 30
interface g1/0/2
ip dhcp snooping limit rate 10
ip arp inspection limit rate 8
Port G1/0/2 is configured with a rate of 8 messages for each (default) burst (interval) of 1 second.
interface g1/0/3
ip dhcp snooping limit rate 2
ip arp inspection limit rate 8 burst interval 4
Port G1/0/3 is configured with a rate of 8 over a burst of 4 seconds.
*Configure optional DAI message validation checks
Configure the ip arp inspection validate {[dst-mac] [src-mac] [ip]} global command to add DAI validation steps.
SW(config)#ip arp inspection validate ?
dst-mac (validate destination MAC address)
ip (validate source IP address)
src-mac (validate source MAC address)
2. Verification commands
show ip arp inspection [interfaces]
→to list configuration settings for DAI as well as counters for ARP messages processed and filtered
show ip dhcp snooping binding
→to display the contents of the dynamically created DHCP snooping binding table
show ip arp inspection statistics
→to list the subset of the show ip arp inspection command output that includes counters
Free CCNA | Dynamic ARP Inspection | Day 51 Lab – Notes
Practice quiz questions
You can find four quiz questions and answers for this lesson in Odom, 2020, pp. 404-405.
Key references
Odom, W. (2020). Chapter 8. DHCP Snooping and ARP Inspection, CCNA 200-301 Official Cert Guide (pp. 401-449), Volume 2. Cisco Press.
Related content
Compliance frameworks and industry standards
DHCP snooping configuration and verification
How data flow through the Internet
How to break into information security
IT career paths – everything you need to know
Job roles in IT and cybersecurity
Switch port security configuration and verification
The GRC approach to managing cybersecurity
The Security Operations Center (SOC) career path
Back to DTI Courses



