This lesson constitutes Part 3 of 4 of the wireless networking series of lessons for the CCNA. This lesson focuses on wireless network security and explores various methods for securing a wireless network. Part 1, Wireless fundamentals for the CCNA, covered how a single access point (AP) can provide a basic service set (BSS) for a cell area, and how multiple APs can be connected to form an extended service set (ESS) for a larger network. Part 2, Cisco wireless architectures and AP modes, compared Cisco wireless architectures and AP modes. Part 4, Configure WLAN within the GUI using WPA2 PSK, explains how to configure and verify WLAN within the GUI using WPA2 PSK.
Unlike in a wired connection, in a wireless connection data traveling over the air can be overheard by anyone within range. A comprehensive approach to securing a wireless network focuses on identifying the endpoints of a wireless connection, identifying the end user, protecting the wireless data from eavesdroppers, and protecting the wireless data from tampering. Identifying clients is done via various authentication schemes. Protecting wireless data involves using encryption and frame authentication. This lesson covers a lot of authentication methods and encryption and message integrity algorithms. Specifically, this lesson focuses on topics listed under Section 1, Network Fundamentals, and Section 5, Security Fundamentals, of the CCNA exam topics list, i.e., 1.11 Describe wireless principles: 1.11.d Encryption, and 5.9 Describe wireless security protocols (WPA, WPA2, and WPA3). This post constitutes Issue 43 of my CCNA 200-301 study notes.
- Introduction to wireless security
- Wireless security framework
- Authentication
- Message privacy
- Message integrity
- Wireless client authentication methods
- Open authentication
- WEP (Wired Equivalent Privacy)
- 802.1x/EAP (Extensible Authentication Protocol)
- EAP-based authentication methods
- LEAP (Lightweight EAP)
- EAP-FAST (Flexible Authentication by Secure Tunneling)
- PEAP (Protected EAP)
- EAP-TLS (EAP Transport Layer Security)
- Wireless privacy and integrity methods
- TKIP (Temporal Key Integrity Protocol)
- CCMP (Counter/CBC-MAC Protocol)
- GCMP (Galois/Counter Mode Protocol)
- WPA, WPA2, and WPA3
- Lesson review
- Key wireless security terms
- Practice quiz questions
- Key references
You may also be interested in CCNA wireless networking portal.
Introduction to wireless security
IEEE 802.11 specifies the Physical layer and MAC protocols for WLANs. As long as wireless clients and APs conform to the 802.11 standard, they can pass data back and forth between each other even on the same channel.
However, not every 802.11 device can be trusted. Transmitted frames travel according to the transmitter’s antenna pattern, potentially reaching any receiver within range.
The open nature of wireless communication makes it vulnerable to eavesdropping and hacking. If you use wireless communication, it is important to take steps to protect your data. Here are some key security measures for protecting your data when using wireless communication:
- Use a strong password for your wireless network.
- Enable encryption on your wireless network.
- Keep your wireless devices up to date with the latest security patches.
- If you are not sure if a SSID is legitimate, do not connect to it.
- Avoid using public Wi-Fi networks for sensitive activities, such as online banking or shopping.
- Use a VPN when connecting to public Wi-Fi networks. A VPN will encrypt your traffic, making it more difficult for an attacker to intercept your data.
Wireless security framework
The 802.11 standard provides a wireless security management framework to be used to add trust, privacy, and integrity to a wireless network. The following three subsections (Authentication, Message privacy, and Message integrity) give an overview of the wireless security framework.
Authentication
Recall, clients must first discover a BSS and then request permission to associate with it. Only trusted and expected devices should be given network access to prevent unauthorized exposure of confidential data by some adversary or malicious actor. Guest users, if permitted access, should join a different guest WLAN where they can access nonconfidential resources. Rogue clients should not be permitted to associate at all.
Clients should be authenticated before they are given access to private WLANs – even before they are allowed to associate. Potential clients must present a form of credentials to the APs to identify themselves.
There are several methods of wireless authentication. One common method is to use a shared static text string, also known as a pre-shared key (PSK). The PSK is stored on the client device and is presented to the AP when the client attempts to connect to the network. Any user who possessed the device could authenticate to the network.
More stringent authentication methods require interaction with a user database, with the end user entering a valid username and password.
When you connect to a wireless network, the only information you typically have is the network name (SSID). If the SSID looks familiar, you will likely connect to it. You generally expect the AP that is advertising the SSID to be owned and operated by the entity where you are located. However, if an imposter is broadcasting the same SSID as a legitimate network, you may unwittingly connect to the imposter’s network.
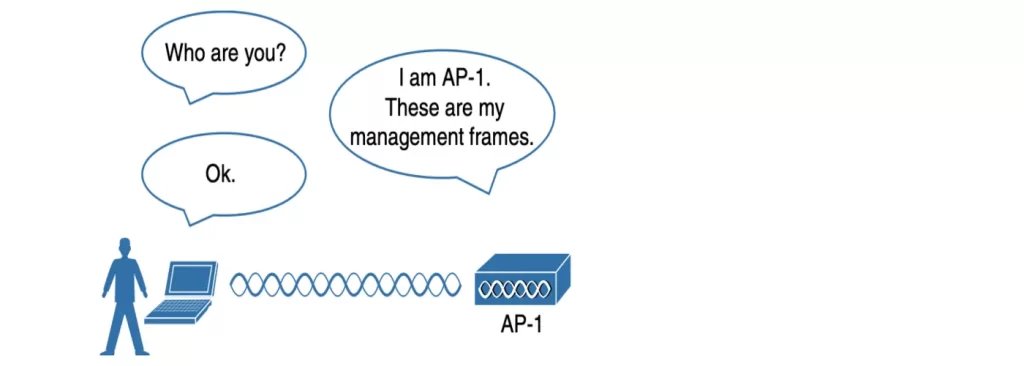
Some common attacks focus on a malicious user pretending to be an AP. The fake AP can send beacons, answer probes, and associate clients just like the real AP it is impersonating. Once a client associates with the fake AP, the attacker can easily intercept all communication to and from the client from its central position. A fake AP could also send spoofed management frames to disassociate or deauthenticate legitimate and active clients, just to disrupt normal network operation. (Odom, 2020, p. 708)
This attack type can be prevented by requiring the client to authenticate the AP before the client itself is authenticated. Figure 28-3 demonstrates the basic authentication idea. Management frames received by a client should also be authenticated as proof that they were sent by a legitimate and expected AP.
Message privacy
The client in Figure 28-3 has to authenticate to join the wireless network. Before it is itself authenticated, the client authenticates the AP and its management frames. While the client’s relationship with the AP would become more trusted, coming and going traffic to the client is still susceptible to eavesdroppers on the same channel.
To protect data privacy on a wireless network, the data must be encrypted while it is traveling between clients and APs. This is done by encrypting the data payload in each wireless frame just before it is transmitted, and then decrypting it as it is received. The encryption method must be one that the transmitter and receiver share, so that the data can be encrypted and decrypted successfully.
Wi-Fi Protected Access (WPA) is a security protocol that uses a pre-shared key (PSK) to encrypt data to protect data transmitted over wireless networks.
Each WLAN may support only one authentication and encryption standard. The AP should securely generate a unique encryption key for each client device associated with the network. This will help to protect the data that is transmitted between the AP and the client devices.
Ideally, the AP and a client are the only two devices that have the encryption keys in common so that they can understand each other’s data. No other device should know about or be able to use the same keys to eavesdrop and decrypt the data. (p. 709)
In Figure 28-4, the client’s confidential password information is protected by encryption before it is transmitted over the wireless network. The AP can decrypt the password information successfully before forwarding it to the wired network. However, other wireless devices cannot decrypt the password information.
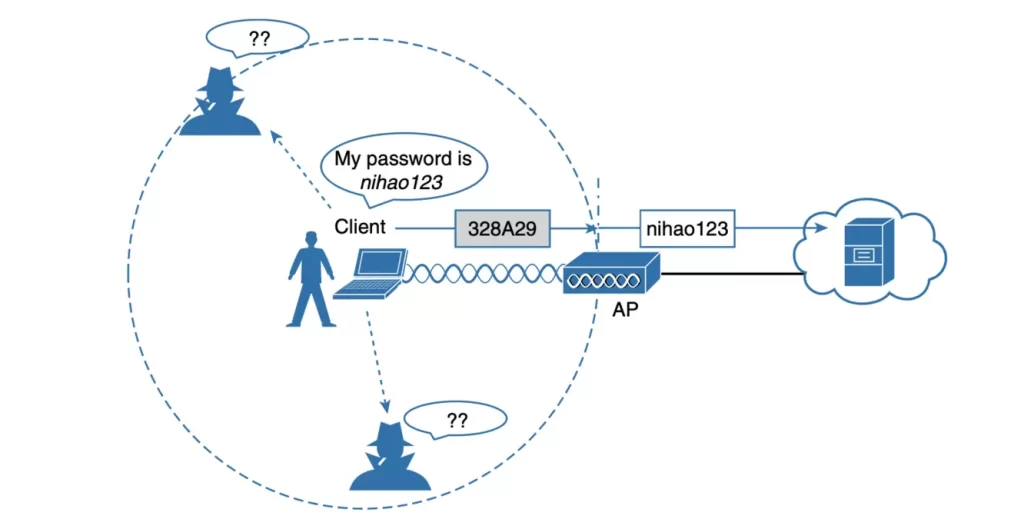
Further, the AP maintains a group key that it uses to send encrypted data to all clients in its coverage area at one time. Each client device that is associated with the AP uses the same shared key to decrypt the data.
Message integrity
Encrypting data can protect the confidentiality of data by scrambling it, obscuring it from view while it is traveling over an untrusted network. The recipient decrypts the data and recovers the message. But someone may still intercept a sent frame and alter its contents. The recipient may not even know that this has happened.
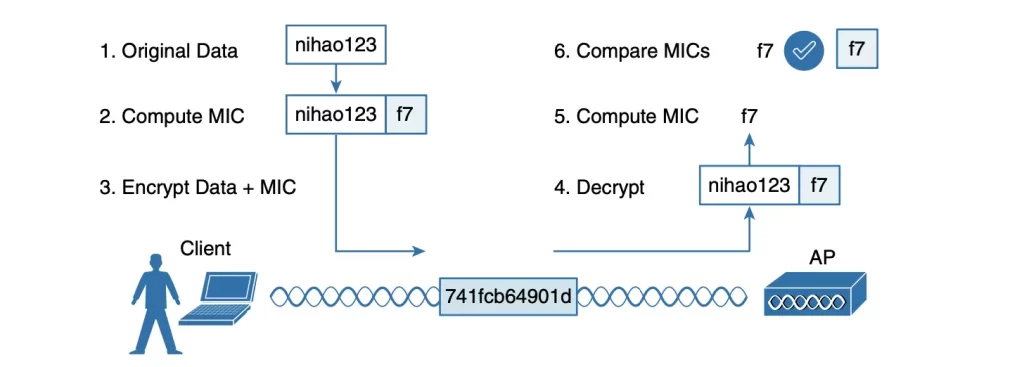
A message integrity check (MIC) is a security tool that can protect against data tampering. A MIC is a value that is calculated from the data in a message using a cryptographic algorithm. The MIC is then sent along with the message. When the message is received, the MIC is recalculated and compared to the value that was sent. If the two values do not match, then the message has been tampered with.
There are two main types of MICs:
- Hash functions: these calculate a value that is a fixed size, regardless of the size of the data that is hashed.
- Message authentication codes (MACs): these calculate a value that is the same size as the data that is being protected.
MICs can be used to protect data in a variety of ways. For example, they can be used to:
- Verify the integrity of files that are downloaded from the internet.
- Protect data that is being transmitted over a network.
- Prevent unauthorized access to data.
MICs are an important part of many security protocols. For example, they are used in the Transport Layer Security (TLS) protocol, which is used to secure web traffic.
MICs are often used in conjunction with encryption to provide a higher level of security. But MICs are not perfect, and they can be fooled by attackers who have access to the cryptographic algorithm. Figure 28-5 shows the MIC process.
Wireless client authentication methods
The original 802.11 standard gave only two options to authenticate clients: open authentication and WEP. The following subsections (Open authentication, WEP, 802.1x/EAP, and EAP-based authentication methods) give an overview of the wireless client authentication methods.
Open authentication
The open authentication process has only one requirement for a client wishing to access a WLAN, that they must use an 802.11 authentication request before attempting to associate with an AP. No other credentials are needed.
With no challenge, any 802.11 client may authenticate to access the network. That is, in fact, the whole purpose of open authentication—to validate that a client is a valid 802.11 device by authenticating the wireless hardware and the protocol. Authenticating the user’s identity is handled as a true security process through other means. (p. 710)
Client screening in WLANs with open authentication will often be a form of web authentication. Most client operating systems will flag WLANs with open authentication to warn you that your wireless data will not be secured in any way if you join.
WEP (Wired Equivalent Privacy)
Wired Equivalent Privacy (WEP) is a wireless security protocol traditionally specified in the 802.11 standard as a method to make a wireless link more like or equivalent to a wired connection.
WEP uses the RC4 cipher algorithm to encrypt data that is transmitted over a wireless network. “The same algorithm encrypts data at the sender and decrypts it at the receiver. The algorithm uses a string of bits as a key, commonly called a WEP key, to derive other encryption keys—one per wireless frame” (p. 711).
WEP uses a shared key that must be known to both the sender and receiver ahead of time in order to encrypt and decrypt data. WEP keys are either 40 or 104 bits in length, represented by a string of 10 or 26 hex digits. Every potential client and AP must share the same key before any client can associate with the AP.
Beside its application as an encryption tool, the WEP key can also be used as an optional authentication method. A client not using the correct WEP key cannot associate with an AP.
The AP tests the client’s knowledge of the WEP key by sending it a random challenge phrase. The client encrypts the challenge phrase with WEP and returns the result to the AP. The AP can compare the client’s encryption with its own to see whether the two WEP keys yield identical results. (p. 711)
Weaknesses in the WEP protocol as the protocol is traditionally defined in the 802.11 standard were discovered in 2001, and work began to find better wireless security methods. WEP was officially deprecated in 2004 following the 802.11i amendment ratification. Today, both WEP encryption and WEP shared-key authentication are widely considered to be weak methods to secure a WLAN. There are newer security protocols, such as WPA or WPA2, that are considered more secure than WEP.
802.1x/EAP (Extensible Authentication Protocol)
Client authentication typically involves a challenge-response mechanism, in which the client is presented with a challenge and must provide a correct response in order to be authenticated. Client authentication can also involve the exchange of session or encryption keys.
The deprecation of WEP in 2004 meant a more secure authentication method was needed. The Extensible Authentication Protocol (EAP) is a flexible and scalable authentication framework. “EAP defines a set of common functions that actual authentication methods can use to authenticate users” (p. 712). EAP can integrate with the IEEE 802.1x port-based access control standard.
When 802.1x is enabled, for a wireless client to gain access to the network, the client must first associate with an AP and then successfully authenticate. The client uses open authentication to associate with the AP, and then the actual client authentication occurs at a dedicated authentication server. This is different from open and WEP authentication where wireless clients are authenticated locally at the AP without further intervention.
The three-party 802.1x arrangement involves of the following entities:
■ Supplicant: The client device requesting access.
■ Authenticator: The network device providing (controlling) access to the network, a LAN switch or a WLC.
■ Authentication server (AS): The device that takes client credentials and permits or denies network access based on a user database and policies (usually a RADIUS server).
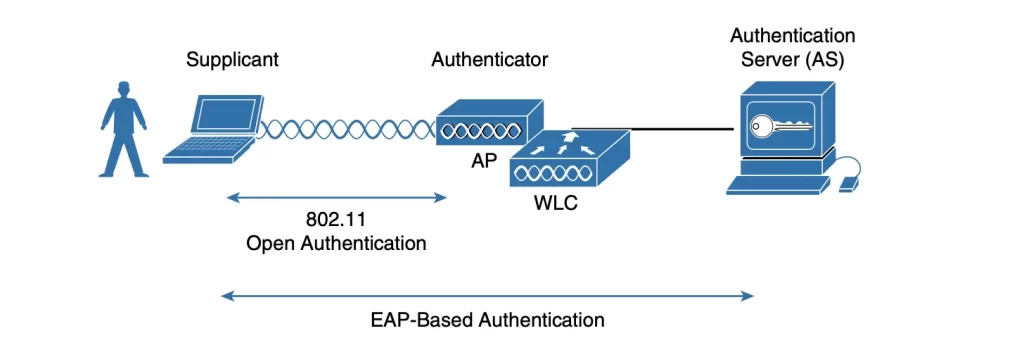
The WLC acts as a middleman in the client authentication process, controlling user access according to 802.1x and communicating with the authentication server using the EAP framework.
The client authentication process involving a WLC is as follows:
- The client device sends a wireless association request to the AP.
- The AP forwards the request to the WLC.
- The WLC authenticates the client device via a RADIUS server.
- If the client device is authenticated successfully, the WLC grants access to the network.
- The client device can then start sending and receiving data on the network.
The RADIUS server uses a variety of authentication methods, such as passwords, certificates, and biometrics.
What’s a supplicant again?
In computer networking, a supplicant is an entity at one end of a point-to-point LAN segment that seeks to be authenticated by an authenticator attached to the other end of that link. The IEEE 802.1X standard uses the term “supplicant” to refer either to hardware or to software. In practice, a supplicant is a software application installed on an end-user’s computer. The user invokes the supplicant and submits credentials to connect the computer to a secure network. If the authentication succeeds, the authenticator typically allows the computer to connect to the network. wikipedia.org/wiki/Supplicant_(computer)
So, the client is the device that is trying to connect to the network, while the supplicant is the software on the client that is responsible for actually authenticating with the network.
The WLC uses the RADIUS server to authenticate client devices because it is a more secure and scalable approach to protecting wireless networks from unauthorized access than authenticating client devices directly on the AP. The RADIUS server can be located in a central location, which makes it easier to manage and secure. Additionally, the RADIUS server can support a large number of client devices, which is ideal for large networks.
Benefits of using a WLC for client authentication include:
- Centralized management: WLCs allow network administrators to manage all of their APs from a single location. This can save time and effort, and it can also help to improve security.
- Increased scalability: WLCs can support more APs than standalone APs. This makes them ideal for large networks.
- Improved performance: WLCs can improve the performance of wireless networks by offloading some of the processing tasks from the APs.
- Robust security: WLCs can use a variety of authentication methods, such as passwords, certificates, and biometrics. This makes them a more secure solution than authenticating client devices directly on the AP.
EAP-based authentication methods
The following discussion gives an overview of some common EAP-based authentication methods.
Note, when configuring user authentication on a WLAN, you do not need to select a specific authentication method. Instead, you select 802.1x on the WLC. This will allow the WLC to handle a variety of EAP methods. The client and authentication server will then use a compatible method. Once 802.1X is enabled on the WLC, the client and authentication server will negotiate a method to use. Configuring security on a WLAN is the topic of the next lesson.
*LEAP (Lightweight EAP)
Lightweight Extensible Authentication Protocol (LEAP) is a wireless authentication method that uses challenge-response messages to authenticate clients. LEAP was developed by Cisco in an early attempt to address the weaknesses in WEP.
The client sends its username and password to the authentication server, which then generates a challenge message and sends it back to the client. The client encrypts the challenge message using its password and sends it back to the authentication server. The authentication server then decrypts the challenge message and compares it to the original challenge message. If the messages match, the authentication server grants access to the client.
This process provides mutual authentication because both the client and the authentication server must be able to successfully decrypt the challenge messages. If either party is unable to decrypt the messages, the authentication will fail.
LEAP attempted to overcome WEP weaknesses by using dynamic WEP keys that changed frequently. Nevertheless, the method used to encrypt the challenge messages was found to be vulnerable, so LEAP has since been deprecated. (p. 713)
Wireless clients and controllers may still offer LEAP, but you should not use it.
*EAP-FAST (EAP Flexible Authentication by Secure Tunneling)
In Cisco’s more secure authentication method called EAP Flexible Authentication by Secure Tunneling (EAP-FAST), authentication credentials are protected by passing a protected access credential (PAC) between the AS and the supplicant. The PAC is a shared secret generated by the AS and used for mutual authentication.
EAP-FAST constitutes of a sequence of three phases:
■ Phase 0: The PAC is generated by the AS and installed on the client.
■ Phase 1: The supplicant and AS authenticate each other and then they negotiate a Transport Layer Security (TLS) tunnel.
■ Phase 2: The end user can then be authenticated through the TLS tunnel.
Like in other EAP-based authentication, a RADIUS server (AS) is required. However, the RADIUS server must also operate as an EAP-FAST server to be able to generate PACs, one per user.
*PEAP (Protected EAP)
The Protected EAP (PEAP) method, like EAP-FAST, uses an inner authentication (inside the TLS tunnel) and outer authentication (outside the TLS tunnel), but in the outer authentication the AS presents a digital certificate to authenticate itself with the supplicant. If the supplicant authenticates the AS, they both build a TLS tunnel to be used for the inner client authentication and encryption key exchange.
The digital certificate of the AS consists of data in a standard format that identifies the owner and is “signed” or validated by a third party. The third party is known as a certificate authority (CA) and is known and trusted by both the AS and the supplicants. The supplicant must also possess the CA certificate just so that it can validate the one it receives from the AS. The certificate is also used to pass a public key, in plain view, which can be used to help decrypt messages from the AS. (p. 713)
In this process, only the AS has a certificate for PEAP, so the supplicant can readily authenticate the AS. Since the client does not use a certificate of its own, the client must be authenticated within the TLS tunnel via one of the following two methods:
■ MSCHAPv2: Microsoft Challenge Authentication Protocol version 2.
■ GTC: Generic Token Card; a hardware device that generates one-time passwords for the user or a manually generated password.
*EAP-TLS (EAP Transport Layer Security)
PEAP uses a digital certificate on the AS to authenticate the RADIUS server. The clients have to identify themselves through other means. EAP Transport Layer Security (EAP- TLS) goes one step above PEAP by requiring certificates on the AS and on every client device. With EAP-TLS, the AS and the supplicant exchange certificates and authenticate each other. A TLS tunnel is then built to exchange encryption key material.
EAP-TLS is considered “the most secure wireless authentication method available” but its implementation can be complex.
Along with the AS, each wireless client must obtain and install a certificate. Manually installing certificates on hundreds or thousands of clients can be impractical. Instead, you would need to implement a Public Key Infrastructure (PKI) that could supply certificates securely and efficiently and revoke them when a client or user should no longer have access to the network. (p. 714)
EAP-TLS can only be used if the wireless clients can accept and use digital certificates.
Wireless privacy and integrity methods
The original 802.11 standard supported only WEP to secure wireless data from eavesdroppers. As noted, WEP has been deprecated for its weakness. Other options are available to encrypt data and protect its integrity as it travels through free space.
TKIP (Temporal Key Integrity Protocol)
Temporal Key Integrity Protocol (TKIP) was designed by the IEEE 802.11i task group and the Wi-Fi Alliance as an interim solution to replace WEP without requiring the replacement of legacy hardware. Under WEP it was possible to alter a packet whose content was known even if it had not been decrypted. The breaking of WEP had left Wi-Fi networks without viable link-layer security, and a solution was required for already deployed hardware.
To be able to run on legacy WEP hardware with minor upgrades, TKIP uses RC4 as its cipher. TKIP also provides a rekeying mechanism. TKIP ensures that every data packet is sent with a unique encryption key (Interim Key/Temporal Key + Packet Sequence Counter). Key mixing increases the complexity of decoding the keys by giving an attacker substantially less data that has been encrypted using any one key.
TKIP brought the following security features using legacy hardware and the underlying WEP encryption (pp. 714-715):
■ MIC: This efficient algorithm adds a hash value to each frame as a message integrity check to prevent tampering; commonly called “Michael” as an informal reference to MIC.
■ Time stamp: A time stamp is added into the MIC to prevent replay attacks that attempt to reuse or replay frames that have already been sent.
■ Sender’s MAC address: The MIC also includes the sender’s MAC address as evidence of the frame source.
■ TKIP sequence counter: This feature provides a record of frames sent by a unique MAC address, to prevent frames from being replayed as an attack.
■ Key mixing algorithm: This algorithm computes a unique 128-bit WEP key for each frame.
■ Longer initialization vector (IV): The IV size is doubled from 24 to 48 bits, making it virtually impossible to exhaust all WEP keys by brute-force calculation.
TKIP became a stopgap measure to enable stronger encryption on WEP-supporting hardware until the 802.11i standard could be ratified. However, TKIP itself is no longer considered secure, and was deprecated in the 2012 revision of the 802.11 standard.
CCMP (Counter/CBC-MAC Protocol)
The Counter/CBC-MAC Protocol (CCMP) is considered more secure than TKIP. CCMP consists of two algorithms:
■ AES (Advanced Encryption Standard) counter mode encryption.
■ Cipher Block Chaining Message Authentication Code (CBC-MAC) used as a message integrity check (MIC).
AES is open, publicly accessible, and is the most secure encryption method available today. AES is widely used around the world. AES is the encryption algorithm of choice for NIST and the U.S. government today.
CCMP cannot be used on legacy devices that only support WEP or TKIP. For CCMP to be used in a wireless network, the client devices and APs must support the AES counter mode and CBC-MAC in hardware.
Devices that support CCMP have the WPA2 designation.
GCMP (Galois/Counter Mode Protocol)
The Galois/Counter Mode Protocol (GCMP) is a cryptographic protocol that provides confidentiality and integrity for data in wireless networks. It is used in the IEEE 802.11i standard for wireless security, and is also supported by some other wireless networking standards.
GCMP is an authenticated encryption suite that is more secure and more efficient than CCMP. GCMP consists of two algorithms:
■ AES counter mode encryption.
■ Galois Message Authentication Code (GMAC) used as a message integrity check (MIC).
GCMP is used in WPA3.
WPA, WPA2, and WPA3
You want to configure a WLAN with wireless security. As a network admin/engineer, how do you go about selecting compatible authentication and encryption schemes to meet your access control and data security goals?
Through its Wi-Fi Protected Access (WPA) industry certifications, the Wi-Fi Alliance, a nonprofit wireless industry association, worked out straightforward ways to do that:
- Wireless products are tested against stringent criteria that ensure correct implementation of a standard.
- A wireless client device and an AP and its associated WLC certified by the Wi-Fi Alliance for the same WPA version are compatible and offer the same security components.
There are three WPA versions: WPA, WPA2, and WPA3.
The first generation WPA certification (known simply as WPA) was introduced while the IEEE 802.11i amendment for best practice security methods was still under development. The Wi-Fi Alliance based WPA on parts of 802.11i and included 802.1x authentication, TKIP, and a method for dynamic encryption key management.
The Wi-Fi Alliance incorporated the full IEEE 802.11i standard into its WPA2 certification after it was ratified and published. WPA2 uses the superior AES CCMP algorithms instead of the deprecated TKIP algorithms from WPA. It should be clear that WPA2 was intended to replace WPA.
Here are some of the key differences between WPA and WPA2:
- Encryption: WPA uses the TKIP encryption algorithm, which has been shown to have security vulnerabilities. WPA2 uses the AES CCMP encryption algorithm, which is considered to be much more secure.
- Authentication: WPA uses the Pre-Shared Key (PSK) authentication method, which is not as secure as the 802.1X authentication method used by WPA2.
- Robustness: WPA2 is more robust than WPA and is less susceptible to attacks.
The Wi-Fi Alliance introduced WPA3 in 2018, adding several important and superior security mechanisms. WPA3 uses stronger AES encryption with the Galois/Counter Mode Protocol (GCMP). WPA3 also uses Protected Management Frames (PMF) to secure important 802.11 management frames between APs and clients. This prevents malicious activity targeting a BSS’s operation.
If you are using WPA, you should consider using WPA2 instead—at least until WPA3 becomes widely available on wireless client devices, APs, and WLCs.
Table 28-2 Comparing WPA, WPA2, and WPA3 (Odom, 2020, p. 716)
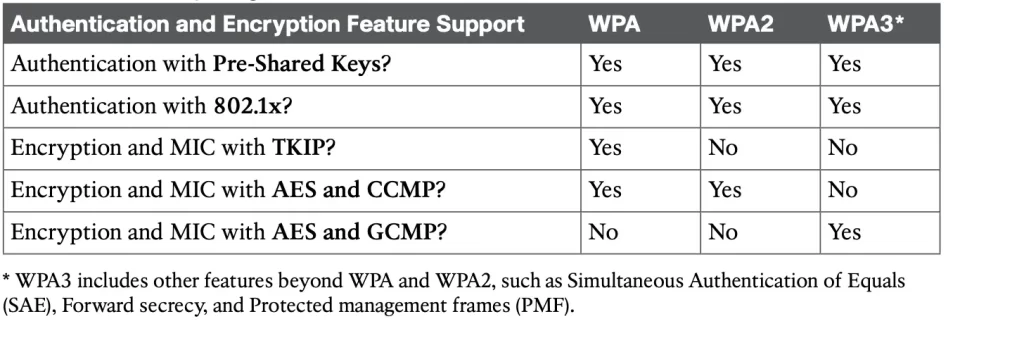
The three WPA versions support two client authentication modes, based on the scale of the deployment:
- A pre-shared key (PSK) or personal mode, or
- 802.1x or enterprise mode
Here is another table comparing WPA, WPA2, and WPA3, in addition to WEP (generated using Bard)
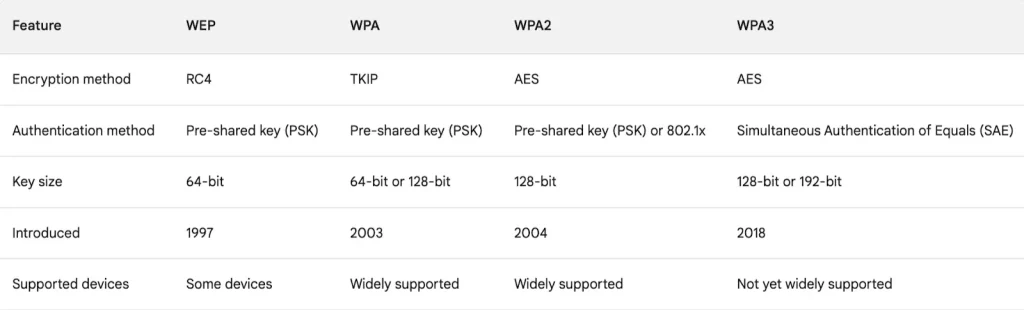
With personal mode, a key string must be shared or configured on every client and AP before the clients can connect to the wireless network. The pre-shared key is normally kept confidential so that unauthorized users have no knowledge of it. The key string is never sent over the air. Instead, clients and APs work through a four-way handshake procedure that uses the pre-shared key string to construct and exchange encryption key material that can be openly exchanged. Once that process is successful, the AP can authenticate the client and the two can secure data frames that are sent over the air. (p. 717)
With WPA-Personal and WPA2-Personal modes, a malicious user can intercept the four-way handshake between a client and an AP and then use a dictionary attack to guess the pre-shared key. If successful, the malicious user can then decrypt the wireless data or join the network as if a legitimate user.
WPA3-Personal can defeat such an attack by strengthening the key exchange between clients and APs using a method known as Simultaneous Authentication of Equals (SAE). “Rather than a client authenticating against a server or AP, the client and AP can initiate the authentication process equally and even simultaneously.
WPA3-Personal offers forward secrecy, so, even if a password or key is compromised, attackers are prevented from being able to use a key to unencrypt data that has already been transmitted over the air.
The Personal mode of any WPA version is easy to deploy in a small environment because a simple text key string is all that is needed to authenticate the clients.
Note that all devices using the WLAN must be configured with an identical pre-shared key. Changing the key means every device using the WLAN must be updated.
Notice from Table 28-2 that WPA, WPA2, and WPA3 also support 802.1x or enterprise authentication. This implies EAP-based authentication, but the WPA versions do not require any specific EAP method. Instead, the Wi-Fi Alliance certifies interoperability with well- known EAP methods like EAP-TLS, PEAP, EAP-TTLS, and EAP-SIM. Enterprise authentication is more complex to deploy than personal mode because authentication servers must be set up and configured as a critical enterprise resource. (p. 717)
The Wi-Fi Alliance made wireless security configuration straightforward and consistent through its WPA, WPA2, and WPA3 certifications.
WPA, WPA2, and WPA3 simplify wireless network configuration and compatibility because they limit which authentication and privacy/integrity methods can be used. See Table 28-3.
Lesson review
Table 28-3 lists the key topics (acronyms and security terms) covered in this lesson. The table is organized in a way that should help you remember how the acronyms and functions are grouped together. Remember that an effective wireless security strategy includes a method to authenticate clients and a method to provide data privacy and integrity. These two types of methods are listed in the leftmost column. Work your way to the right to remember what types of authentication and privacy/integrity are available.(Odom, 2020, p. 718)
Table 28-3 Review of Wireless Security Mechanisms and Options (Odom, 2020, p. 718)
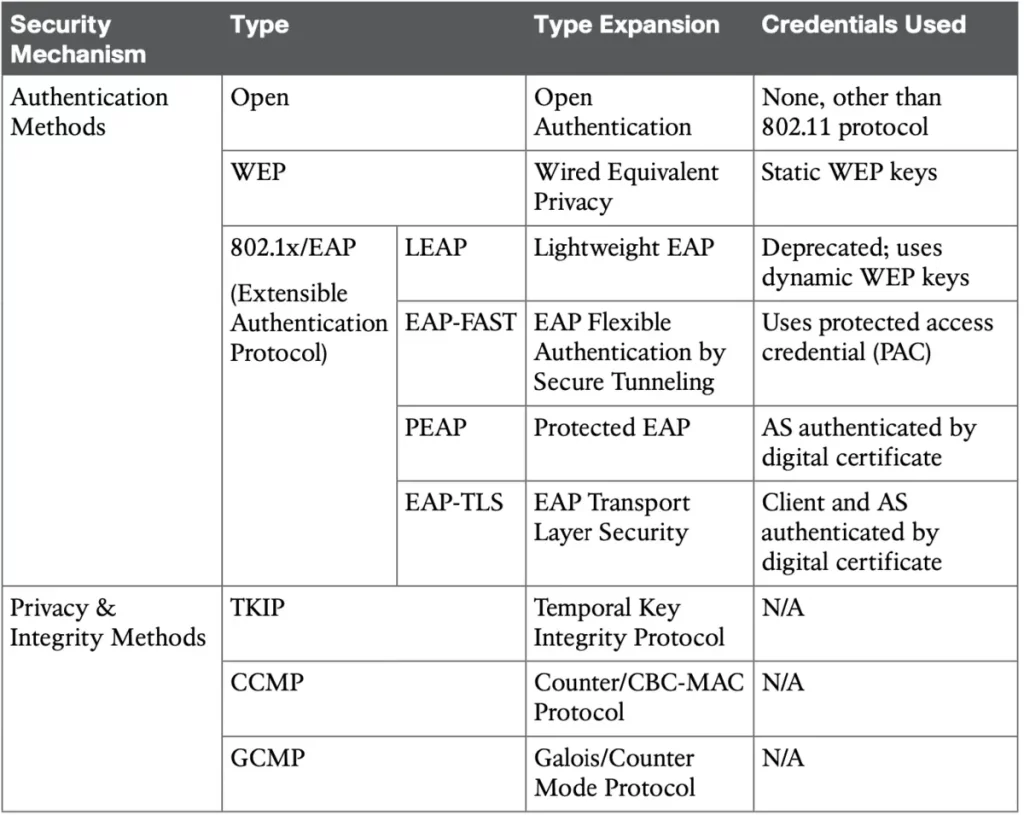
Key wireless security terms
802.1x, authentication server (AS), authenticator, certificate authority (CA), Counter/CBC- MAC Protocol (CCMP), EAP Flexible Authentication by Secure Tunneling (EAP-FAST), EAP Transport Layer Security (EAP-TLS), enterprise mode, Extensible Authentication Protocol (EAP), forward secrecy, Galois/Counter Mode Protocol (GCMP), Lightweight EAP (LEAP), message integrity check (MIC), open authentication, personal mode, protected access cre- dential (PAC), Protected EAP (PEAP), Protected Management Frame (PMF), Public Key Infrastructure (PKI), RADIUS server, Simultaneous Authentication of Equals (SAE), sup- plicant, Temporal Key Integrity Protocol (TKIP), Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), WPA Version 2 (WPA2), WPA Version 3 (WPA3).
Practice quiz questions
You can find four quiz questions and answers for this lesson in Odom, 2020, pp. 704-708.
Key references
Odom, W. (2020). Chapter 28. Securing Wireless Networks, CCNA 200-301 Official Cert Guide (pp. 704-719), Volume 1. Cisco Press.
Related content
Cisco wireless architectures and AP modes
Compliance frameworks and industry standards
Configure WLAN within the GUI using WPA2 PSK
How data flow through the Internet
How to break into information security
How to get started in cryptography – article highlights
IT career paths – everything you need to know
Job roles in IT and cybersecurity
The GRC approach to managing cybersecurity
The Security Operations Center (SOC) career path
Wireless fundamentals for the CCNA
Back to DTI Courses



