The Open Systems Interconnection (OSI) Model
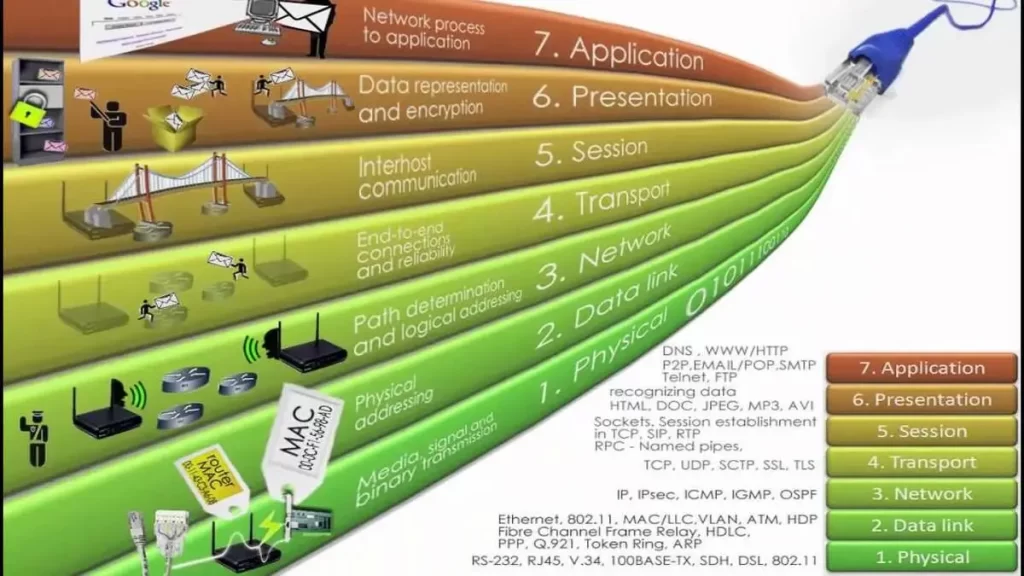
This post discusses the Open Systems Interconnection (OSI) Model. It constitutes Lesson 2 of the module How data flow through the Internet. Key concepts discussed in this post include the OSI model Physical layer, Data Link layer, Network layer, Transport layer, Session layer, Presentation layer, Application layer, and data encapsulation/de-encapsulation. You may also be interested […]
The Open Systems Interconnection (OSI) Model Read More »