Wireless network security
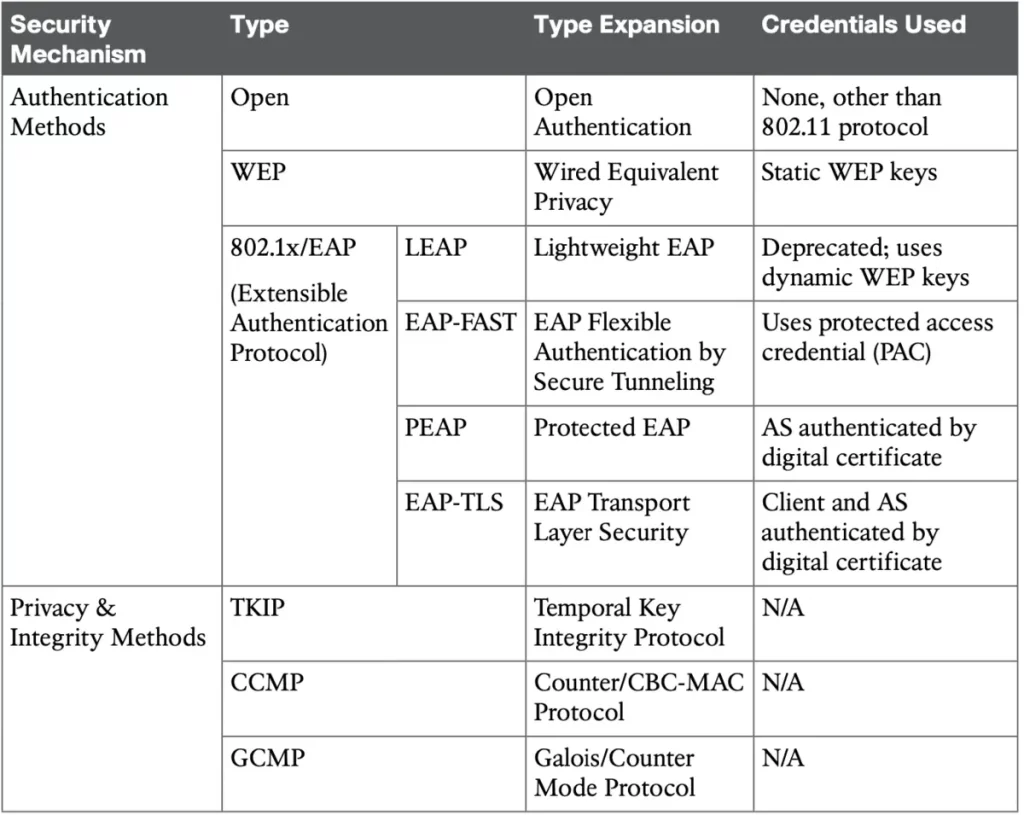
This lesson constitutes Part 3 of 4 of the wireless networking series of lessons for the CCNA. This lesson focuses on wireless network security and explores various methods for securing a wireless network. Part 1, Wireless fundamentals for the CCNA, covered how a single access point (AP) can provide a basic service set (BSS) for […]
Wireless network security Read More »