These CCNA study notes cover a big chunk of the topics listed in Section 5 Security Fundamentals of the CCNA exam blueprint – specifically, subsections 5.1 Define key security concepts (threats, vulnerabilities, exploits, and mitigation techniques), 5.2 Describe security program elements (user awareness, training, and physical access control), 5.4 Describe security password policies elements, such as management, complexity, and password alternatives (multifactor authentication, certificates, and biometrics), and 5.8 Compare authentication, authorization, and accounting concepts.
First, some key security concepts and terms are introduced. Next, common attacks which can target an enterprise’s systems and information are discussed. Next, passwords and multi-factor authentication (MFA) are discussed. Then the concepts of Authentication, Authorization, and Accounting (AAA) are explained. Finally, security program elements for enterprises to secure their systems and educate their staff are discussed. This post constitutes Issue 37 of my CCNA 200-301 study notes.
- Why security (CIA triad)
- Fundamental security concepts
- Common attacks
- Denial of service attacks
- Spoofing attacks
- Reflection and amplification attacks
- Man in the middle attacks
- Reconnaissance attacks
- Malware
- Social engineering attacks
- Password attacks
- Multi-factor authentication
- Digital certificates
- AAA (Authentication, Authorization, and Accounting)
- Security program elements
- Key learnings
- Practice quiz questions
- Key references
You may also be interested in CCNA Security Fundamentals portal.
Why security (CIA triad)
A fundamental goal of security in an enterprise is to protect the confidentiality, integrity, and availability (CIA) of information assets. The principles of the CIA triad form the foundation of security.
- Confidentiality: only authorized users should be able to access privileged/private data.
- Integrity: data should not be changed or modified by unauthorized users. Data should be correct and authentic.
- Availability: the enterprise network and systems should be operational and accessible to authorized users. For example, staff should be able to access the internal resources they need to perform their duties, and the company’s website should be up and running and available to customers.
Fundamental security concepts
In addition to the CIA triad, there are some other fundamental security concepts we need to know. The CCNA exam topics explicitly mentions threats, vulnerabilities, exploits, and mitigation techniques.
- A vulnerability is any potential weakness that can compromise the CIA of a system or information assets. A window in a house is a vulnerability burglars can exploit to enter the house.
- An exploit is something that can potentially be used to exploit the vulnerability. A rock can exploit the weakness of a glass window and may be used to enter a house.
- A threat is the potential of a vulnerability to be exploited. A threat is a robber who can use a rock to break a glass window and enter your house. A hacker exploiting a vulnerability in your computer network is a threat.
- A mitigation technique is something that can protect against threats. There are various mitigation techniques and they depend on the threat that is being mitigated.
Appropriate mitigation techniques should be implemented everywhere a vulnerability can be exploited, for example client devices, servers, switches, routers, and firewalls. Mitigation techniques also include preventing unauthorized people from getting physical access to the devices, for example, by keeping them in a secure rack behind a secure door.
Systems can be more secure or less secure, but there are no guarantees in security. You can implement malware detection on your network firewall and have the best antivirus software on client PCs, but the chance of the PCs getting infected with malware is never 0.
Common attacks
Attack types are threats which can potentially exploit vulnerabilities to compromise the CIA of an enterprise’s information assets and network system.
We explore how attackers can threaten the CIA of enterprise systems and information by looking at the following common types of attacks: Denial of service (DoS) attacks, Spoofing attacks, Reflection/amplification attacks, Man in the middle attacks, Reconnaissance attacks, Malware, Social engineering attacks, and Password-related attacks. There are many more potential attacks than these, but these are some of the main attack categories.
Denial of service attacks
DoS attacks threaten the availability of a system. There are many types of DoS attacks, such as SYN flood, UDP flood, HTTP flood, and Ping of death.
The TCP SYN flood is a common type of DoS attack which exploits the TCP three-way handshake process.
The three-way handshake is SYN, SYN-ACK, and ACK. The attacker sends a large number of SYN packets to a target server. The target sends a SYN-ACK message in response to each SYN it receives. But the attacker never replies with the final ACK of the handshake.
The target waits for the final ACK of each handshake, and the incomplete connections fill up the target’s TCP connection table. The incomplete connections will timeout and be removed from the table after a certain period of time, but the attacker continues sending SYN messages to fill up the table. This exhausts the server’s resources and prevents legitimate users from accessing it.
In the end, the target is no longer able to make legitimate TCP connections because it has reached the maximum number of TCP connections it can maintain.
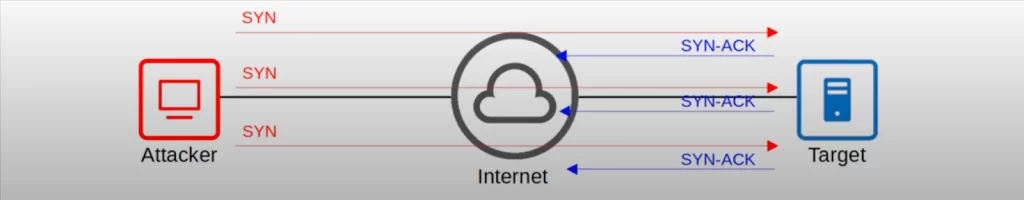
For each SYN message the attacker sends, the target puts an entry in its TCP connection table and sends a SYN-ACK message, then waits for an ACK to complete the connection. But the ACK never comes. The attacker keeps sending SYN messages, and the target keeps sending SYN-ACK messages. Then the target’s TCP connection table fills up, and the denial-of-service has been achieved.
The attacker likely spoofs their IP address, meaning the attacker uses a fake IP address, making this a spoofing attack. The SYN-ACK messages do not return back to the attacker.
The malicious client can either simply not send the expected ACK, or by spoofing the source IP address in the SYN, cause the server to send the SYN-ACK to a falsified IP address – which will not send an ACK because it “knows” that it never sent a SYN. (https://en.wikipedia.org/wiki/SYN_flood)
A much more powerful version of this attack type is the DDoS. In a distributed denial-of-service attack, the attacker infects many target computers with malware and uses the computers to initiate a denial-of-service attack such as a TCP SYN flood attack. The group of infected computers is called a botnet.
The PCs infected with malware together start flooding the target with TCP SYN messages, so the target server is no longer able to respond to legitimate TCP connection requests.
Spoofing attacks
To spoof an address is to use a fake source address, for example a fake IP or MAC address. There are many types of spoofing attacks.
A spoofing attack can be used to launch a DoS attack, attacking the availability of the system.
An example of a spoofing attack is a DHCP exhaustion attack, also known as a DHCP starvation attack. It is similar to the TCP SYN flood attack. An attacker uses spoofed MAC addresses to flood DHCP Discover messages. The target server’s DHCP pool becomes full, resulting in a denial-of-service to other devices which are no longer able to get an IP address.
Attackers send DHCP Discover messages with fake source MAC addresses at a very quick pace. The server will reply to each Discover with a DHCP Offer message, and while it is offering an IP address it will not assign that address to other devices.
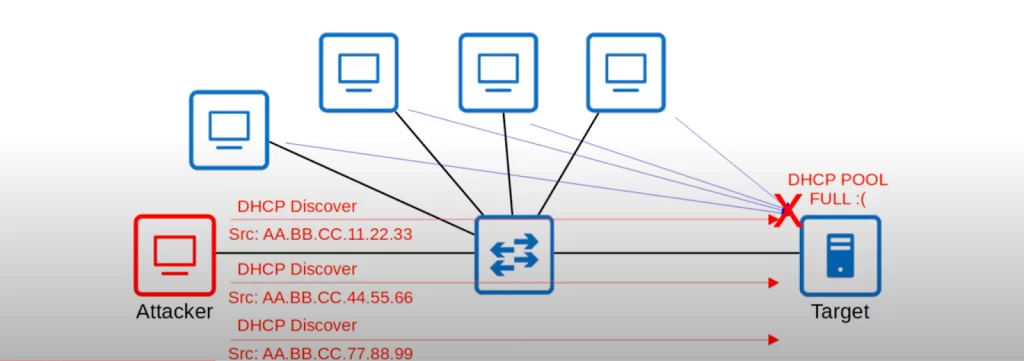
So if some PCs send DHCP Discover messages to get IP addresses, the server is not able to give them their IP addresses because its DHCP pool is full. Maybe it had 250 IP addresses to lease to clients, but they are all taken by the attacker.
In this short video, Keith Barker explains the DHCP starvation attack and how it can be escalated to a man in the middle attack: MicroNuggets: DHCP Starvation Attacks Explained
In this short video, Jeremy McDowell walks us through a short demo in EVE-NG of the DHCP exhaustion attack: Free CCNA | Kali Linux Demo | Day 48 Lab | CCNA 200-301 Complete Course
Both DHCP snooping and switch port security configurations on switches are effective methods of preventing DHCP starvation attacks.
Not all spoofing attacks are DoS attacks. We will look at the man in the middle attack, another type of spoofing attack that targets the confidentiality and integrity of a system, not the availability.
Reflection and amplification attacks
In a reflection attack, the attacker sends traffic to a reflector such as a DNS server and spoofs the source address of the sent packets using the target’s IP address.
Then the reflector sends the reply to the target’s IP address. If the amount of traffic is large enough this can result in a denial-of-service to the target.
There is a more powerful variant of the reflection attack called an amplification attack. A reflection attack becomes an amplification attack when the amount of traffic sent by the attacker is small, but it triggers a large amount of traffic to be sent from the reflector to the target. This triggers a denial of service. For example, there are DNS and NTP vulnerabilities which can be exploited for such amplification attacks.
Man in the middle attacks
In this kind of attack the attacker places himself between the source and destination to eavesdrop on communications or to modify traffic before it reaches the destination. A common example is ARP spoofing, also known as ARP poisoning. This is another kind of spoofing attack.
In an ARP spoofing attack, a host sends an ARP request asking for the MAC address of another device.
PC1 is asking for the MAC address of host 10.0.0.1, which is SRV1. Because ARP request messages are broadcast, the switch floods the frame, so both SRV1 and the attacker receive it. SRV1 sends an ARP reply to PC1.
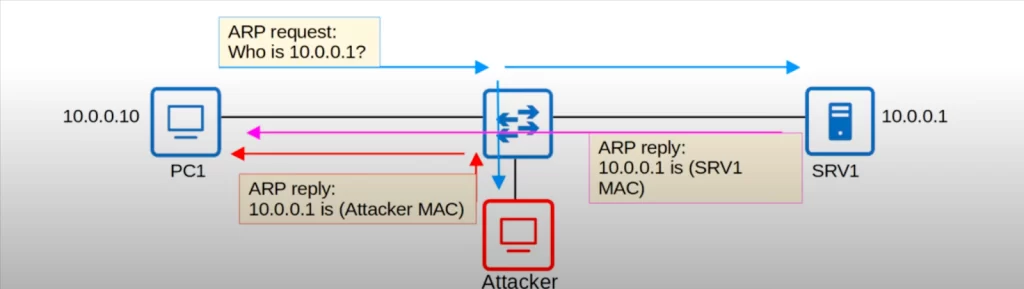
The attacker waits briefly and then sends another ARP reply after the legitimate reply. If the attacker’s ARP reply arrives last, it will overwrite the legitimate ARP entry in PC1’s ARP table.
Now in PC1’s ARP table, the entry for 10.0.0.1 will have the attacker’s MAC address, not the MAC address of the real 10.0.0.1, SRV1. So when PC1 tries to send traffic to SRV1, traffic will be forwarded to the attacker instead. Then, the attacker can inspect the messages, read their contents and then forward them to SRV1. Or the attacker can modify the messages before forwarding them to SRV1.
Reconnaissance attacks
Reconnaissance “attacks” are used to gather information about a target. The information gathered in the initial stage at least is often publicly available information.
For example, you can perform an NSLOOKUP to learn the IP address of a site. From there, you can probe for open ports which are potential vulnerabilities. You could also perform a WHOIS query to learn email addresses, phone numbers, physical addresses, etc. at this website: https://lookup.icann.org/en
The information gathered in this stage can be used to launch a targeted social engineering attack.
Malware
Malware, malicious software, refers to a variety of harmful programs that can infect a computer. There are many types of malware. Here are a few types.
*Viruses are malware that infects other software, called a host program. The virus spreads as the software is shared by users or downloaded from malicious websites. Once the virus has infected a device it can corrupt or modify files on the target computer.
*Worms are different from viruses in that they don’t require a host program. They are standalone malware and are also able to spread on their own, without user interaction. The spread of worms from device to device can congest the network, but in addition to that if the worm has a payload, other malicious code within the worm, it can cause additional harm to target devices.
*A Trojan horse is harmful software disguised as legitimate software. Trojan horses spread through user interaction such as opening email attachments or downloading a file from the Internet.
These types of malware are defined by how the malware infects a system and how it spreads, not the attacks they carry out after infecting the system.
The above malware types can exploit various vulnerabilities to threaten any of the CIA triad aspects of the target device.
Social engineering attacks
Social engineering attacks do not directly exploit a company’s IT systems, instead they exploit the employees.
No matter how many security features you configure on your routers, switches, firewalls, servers, PCs, etc., people are always a vulnerability that can be exploited.
Social engineering attacks involve psychological manipulation to make the target reveal confidential information or perform some action the attacker wants the target to do. As with the previous attack types, there are various kinds of social engineering attacks. Here are a few common ones.
*Phishing involves fraudulent emails that appear to come from a legitimate business, such as your bank or your credit card company. These emails contain links to a fraudulent website that seems legitimate. The website may look identical to the real login page of your bank’s website, for example. Users are told to login to the fake website, therefore providing their login credentials to the attacker.
>Spear phishing is a type of phishing that is more targeted. This can take the form of personalized emails sent to employees of a specific company
>Whaling is another kind of phishing targeted at high-profile individuals, for example a company president.
>Vishing, voice phishing, is phishing performed over the phone. The attacker could pretend to be from the target’s bank or from the IT department in the company. For example, an attacker may impersonate an IT department employee who says they need to know the password to reset it.
>Mishing, SMS phishing, which is phishing performed using SMS text messages to the target’s cell phone.
*Watering hole attacks compromise sites that the target victim frequently visits. If a malicious link is placed on a website the target trusts, they might not hesitate to click it. So, this kind of attack is taking advantage of the user’s trust in the website they frequently visit.
*Tailgating attacks involve entering restricted, secure areas by simply walking in behind an authorized person as they enter. Any company that has restricted areas will have rules against this, but often the target will hold the door open for the attacker to be polite, assuming the attacker is also authorized to enter.
Password attacks
Most systems use a username and password combination to authenticate users. The username itself is often simple and easy to guess, for example the user’s email address. So, often, the strength and secrecy of the password is relied on to provide the necessary security.
However, attackers can learn a user’s password through multiple methods.
First, they could guess the password. A dictionary attack can also be used, in which a program runs through a dictionary, which is a list of common words and passwords, to guess the target’s password. The program tries each word, hoping to find the correct password.
A brute force attack involves trying every possible combination of letters, numbers, and special characters to find the target’s password. This requires a very powerful computer, and if the password is sufficiently strong, the chances of it working are very low, because it takes so much time.
A strong password should contain at least 8 characters, preferably more than 8. The more characters, the harder it is to brute force attack the password.
A strong password should have a mix of uppercase and lowercase letters and a mix of letters and numbers.
It should also have one or more special characters such as question marks, exclamation points, etc.
Finally it should be changed regularly.
Most enterprises will enforce rules like these on their employees, but it’s also recommended that you follow rules like these when making your own personal passwords.
Multi-factor authentication
No matter how secure the password, there is still a chance it gets into the hands of an attacker. That’s why multi-factor authentication is becoming more and more wide-spread.
Multi-factor authentication involves using at least two authentication methods from at least two of the following categories to prove your identity.
First is something you know, for example a username and password combination.
Next is something you have, for example pressing a notification that appears on your phone using an authenticator app, or using a badge that is scanned.
The third is something you are, these are unique characteristics about you. For example, biometrics such as a face scan, palm scan, fingerprint scan, retina scan, etc.
Digital certificates
Another form of authentication involves the use of digital certificates, which are used to prove the identity of the holder of the certificate. Digital certificates are mainly, but not exclusively, used for websites to verify that the website being accessed is legitimate. Entities that want a certificate, for example a company with a website, send a CSR (certificate signing request) to a CA (certificate authority) which will generate and sign the certificate.
It is not uncommon for website hosting platforms to offer free SSL certificates to their clients. By offering “free SSL”, a hosting platform likely refers to providing free digital certificates and the associated encryption of a website traffic.
- Digital Certificate: A file containing information about the website’s identity and a public key used to encrypt communication. The digital certificate is issued by a trusted Certificate Authority (CA) after verifying ownership of the domain.
- SSL/TLS Encryption: This protocol uses the public key from the digital certificate to encrypt data sent between the website and visitors’ browsers. This ensures confidentiality and integrity of the information exchanged.
SSL/TLS secures web traffic between a client and a server through a process called the TLS handshake. Here’s a breakdown of the key steps:
- Initiation: The client initiates the handshake by sending a “Client Hello” message to the server. This message specifies the supported TLS versions and encryption algorithms (cipher suites).
- Server Response: The server replies with a “Server Hello” message containing its chosen TLS version, cipher suite, and a digital certificate. This certificate holds the server’s public key and identifies a trusted Certificate Authority (CA) that issued it.
- Client Verification: The client verifies the certificate by checking its validity period, CA authenticity, and domain name match. If everything checks out, the client trusts the server’s identity.
- Key Exchange: Both sides create a secret session key. The client generates a random secret value that will act as the basis for the session key. The client encrypts this random secret value using the server’s public key obtained from the certificate. Only the server possesses the corresponding private key for its public key. The server uses this private key to decrypt the message from the client, revealing the random secret value. Both the client and server use the same random secret value to derive the final secret session key.
- Secure Connection and Data Exchange: With the shared session key, both client and server can now encrypt all transmitted data using symmetric encryption (faster than asymmetric encryption used for key exchange). This ensures data confidentiality – even if intercepted, it appears scrambled.
When a hosting platform offers free SSL, it is essentially saying it will generate and install a free digital certificate for the domain, and configure the server to use SSL/TLS encryption with the certificate.
When you access a website, modern browsers display a lock key symbol usually to the left of the url field to indicate that the website is secure and has a valid certificate. You should be able to inspect the certificate if you click on the symbol.
AAA (Authentication, Authorization, and Accounting)
AAA stands for Authentication, Authorization, and Accounting. It’s a framework for controlling and monitoring users of a computer system, such as a network.
*Authentication is the process of verifying a user’s identity. When a user logs in, ideally using multi-factor authentication, that’s authentication.
*Authorization is the process of granting the user the appropriate access and permissions. So, granting the user access to some files and services, but restricting access to other files and services, is authorization.
*Accounting is the process of recording the user’s activities on the system. For example, logging when a user makes a change to a file, or recording when a user logs in or logs out, is accounting.
Enterprises typically use an AAA server to provide AAA services. ISE (Identity Services Engine) is Cisco’s AAA server. AAA (network access control) servers typically support the following two AAA protocols: 1) RADIUS (Remote Authentication Dial-In User System), which is an open standard protocol and uses UDP ports 1812 and 1813; and 2) TACACS+ (Terminal Access Controller Access-Control System Plus), which is also an open standard (that was developed by Cisco) and uses TCP port 49.
Security program elements
A security program is an enterprise’s set of security policies and procedures. For the CCNA, there are a few elements we need to be aware of.
User awareness programs are designed to make employees aware of potential security threats and risks. User awareness programs will help make employees aware of all of the cyber threats the company is facing.
For example, a company might send out false phishing emails to make employees click a link and sign in with their login credentials. Employees who are tricked by the false emails will be informed that it is part of a user awareness program, and they should be more careful about phishing emails.
User training programs are more formal than user awareness programs. For example, dedicated training sessions which educate users on the corporate security policies, how to create strong passwords, and how to avoid potential threats. These should happen when employees enter the company, and also at regular intervals during the year.
Physical access control, which protects equipment and data from potential attackers by only allowing authorized users into protected areas such as network closets or data center floors. This is not just to prevent people outside of the organization from gaining access to these areas. Even within the company, access to these areas should be limited to those who need access.
Multifactor locks can protect access to these restricted areas. For example, a door that requires users to swipe a badge and scan their fingerprint to enter. That’s something you have, a badge, and something you are, your fingerprint. Badge systems are very flexible, and permissions granted to a badge can easily be changed. This allows for strict, centralized control of who is authorized to enter where.
Key learnings
*Some key security concepts including the CIA triad as well as vulnerabilities, exploits, threats, and mitigation techniques.
*Common attacks, from common network attacks to social engineering attacks which target people.
*Passwords and multi-factor authentication, which includes a combination of something you know, something you have, and something you are.
*AAA. Authentication is the process of verifying a user’s identity. Authorization is the process of controlling what that user is allowed to do in the system. And Accounting is keeping track of what the user does.
*Some elements of an enterprise’s security programs, such as user awareness, user training, and physical access control.
Practice quiz questions
*You can find five practice questions for this lesson (plus a bonus one) in Jeremy’s Security Fundamentals video, cited below.
Key references
Note: The resources cited below (in the “Key references” section of this document) are the main source of knowledge for these study notes/this lesson, unless stated otherwise.
Free CCNA | Security Fundamentals | Day 48 | CCNA 200-301 Complete Course
Related content
Compliance frameworks and industry standards
DAI configuration and verification
DHCP snooping configuration and verification
How data flow through the Internet
How to break into information security
IT career paths – everything you need to know
Job roles in IT and cybersecurity
Switch port security configuration and verification
The GRC approach to managing cybersecurity
The Security Operations Center (SOC) career path
Back to DTI Courses



