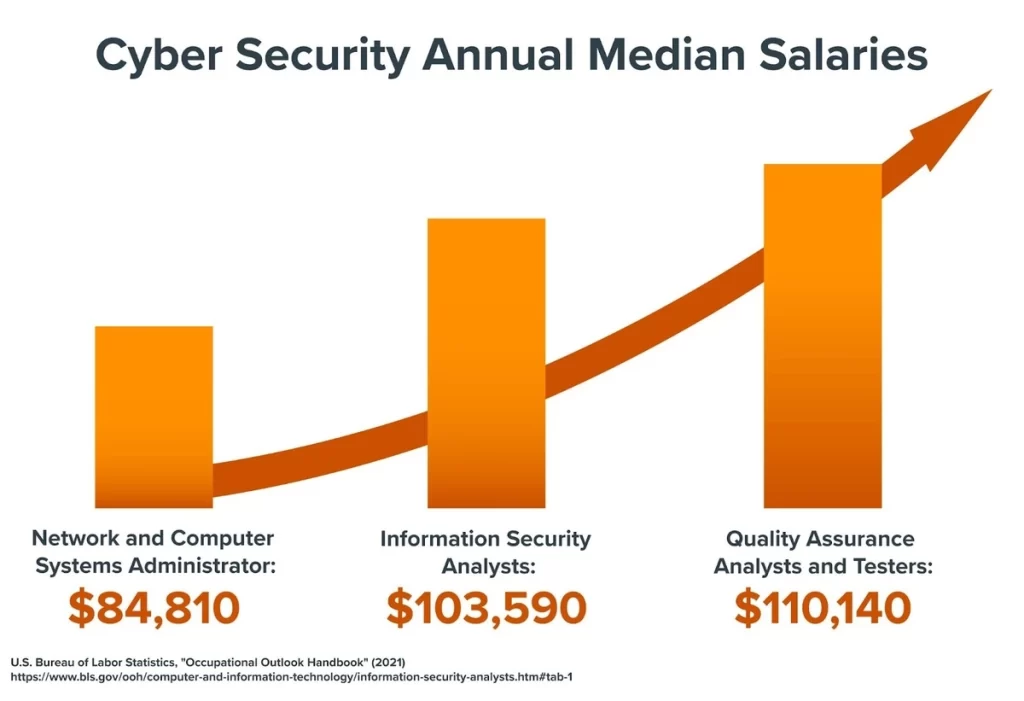
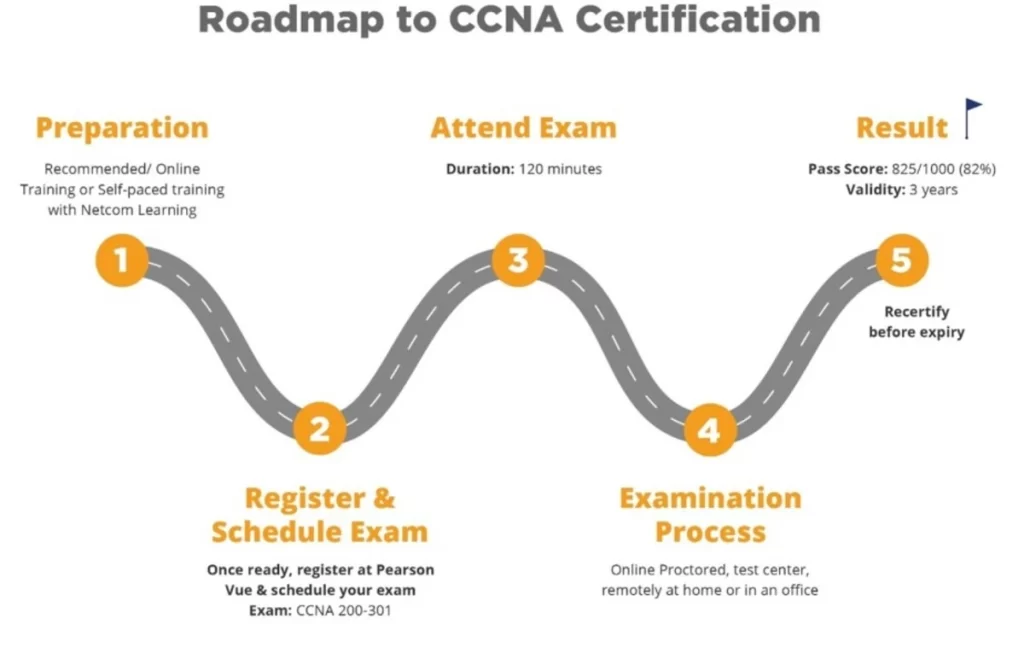
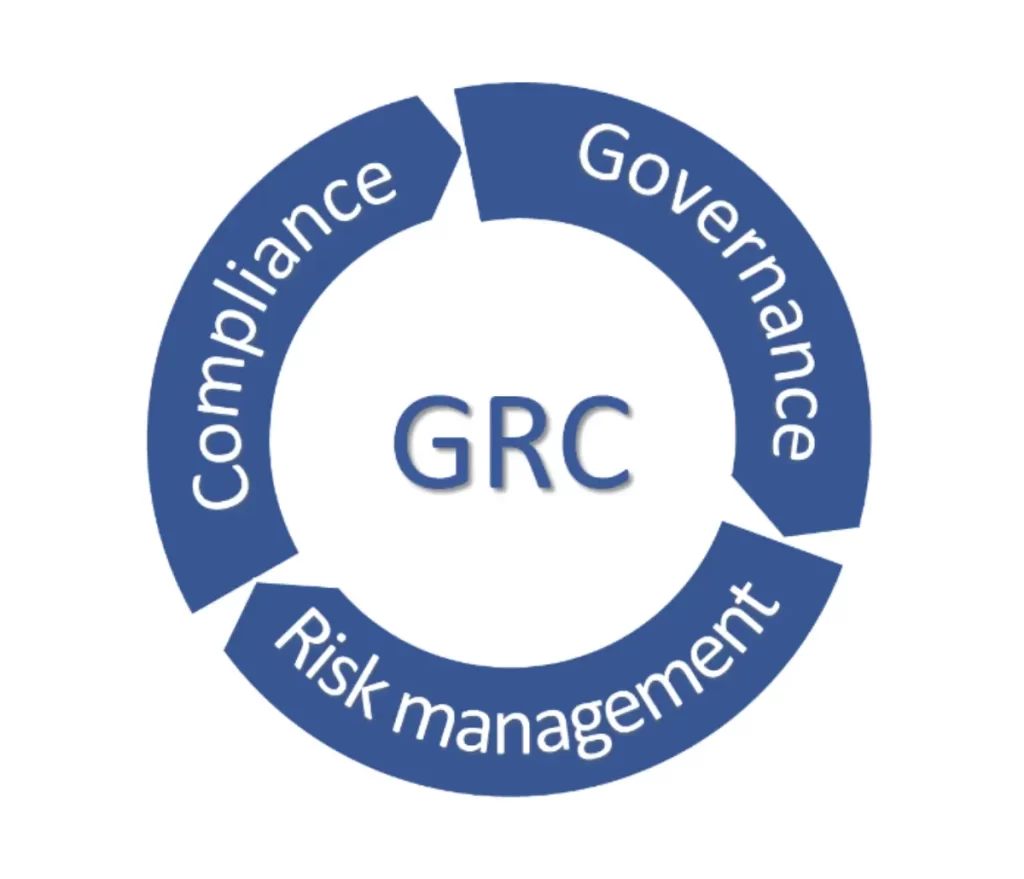
Job roles in IT and cybersecurity
This post gives a succinct overview of in-demand job roles in IT and cybersecurity. Key job responsibilities, skills, and certifications for the following IT and cybersecurity roles are covered: System Administrator, Network Administrator, Incident Responder, Penetration Tester, Cloud Engineer, Cybersecurity Manager, and Privacy Analyst. You may also be interested in IT career paths – everything you […]
Job roles in IT and cybersecurity Read More »