How to get started in cryptography by Shamil Alifov
Fair use disclaimer: I do not own this content. This post contains excerpts (“highlights”) from a longer article used here solely for educational purposes. All credits go to its rightful owner. Please see Citation information.
<In this chapter, I will provide some basic notions of cryptography, provide a list of resources, and suggest some paths to becoming savvy in the field.>
You may also be interested in How to break into information security.
Short introduction
<These four key aspects are the primary goals of cryptography:
• Confidentiality is the property that keeps information secret/non-available to unauthorized parties. For example, you want to send a message to your friend, but do not want anybody else to be able to read it. Thus, you need to apply some magic techniques to make your message unreadable by anyone besides your friend.
• Authentication relates to the identification of a user and data; in other words, it is a process of confirming that the data and user are genuine. As an example, say you get a message from a friend and you want to be sure that the message is really from your friend, not an unknown person who is impersonating your friend.
• Data integrity is related to ensuring that information is not changed or manipulated by unauthorized parties. The focus in on verifying that that the data or message that you’ve received is genuine and hasn’t been altered by an unauthorized third party.
• Non-repudiation prevents a user from denying authorship of actions and information they’ve made. For instance, a friend of yours may promise to join your team in Pokémon Go, then refuse to admit they’d made that promise. To resolve that type of situation, there should be a trusted third party (say, some mutual friend) who will keep track of everybody’s commitments.>
Essential terms
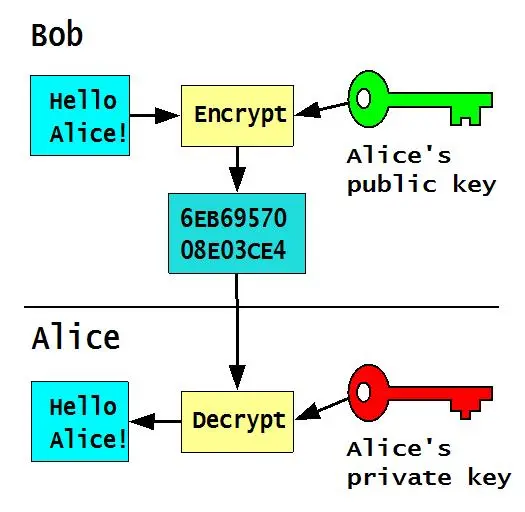
<Encryption is a process of transforming simple text/data, called plaintext, into unintelligible form, named as ciphertext. Decryption is the inverse process of encryption. Cipher is an algorithm that performs encryption/decryption. A key is a secret string of characters or symbols that is used for the encryption/decryption of plaintext/ciphertext. Sometimes, the term cryptosystem is used instead of cipher. There are two types of ciphers depending on the use of keys: symmetric and asymmetric.
Symmetric ciphers, also referred as secret-key ciphers, use the same key for encryption and decryption. Symmetric cryptosystems are divided into two groups: block and stream ciphers. In block ciphers, operations of encryption/decryption are performed on blocks of bits or bytes, whereas stream ciphers operate on individual bits/bytes. Asymmetric ciphers, alternatively named public-key ciphers, use two keys, one for encryption and other for decryption. Cryptanalysis is a study of techniques for “cracking” encryption ciphers, i.e., attacks on cryptosystems. And chances are you’ve heard about hashing algorithms, which involves taking an input of any length and outputting a fixed-length string, called a hash. Which can be used, for example, as signatures or for data-integrity purposes.>
List of resources
<If you’re just getting interested in the field, a good starting point for reading about cryptographyrelated topics is Wikipedia’s Cryptography Portal. >
Top blogs
A Few Thoughts on Cryptographic Engineering – From Mathew Green, a cryptographer and professor at Johns Hopkins University.
Schneier on Security – Bruce Schneier’s blog.
Bristol Cryptography Blog – Official blog of Bristol University’s cryptography research group.
Outsourced Bits – Blog of Seny Kamara, associate professor of computer science at Brown University.
Light Blue Touchpaper – a blog of a security group at the University of Cambridge.
Ellipticnews – All about advances in elliptic curve cryptography.
Learning crypto
<There are basically two ways of getting started in cryptography, either earning a master’s/PhD degree in the field, or through self-study. Obviously, the latter path is way more challenging, so I’ll offer some tips for self-learners.
Associate professor of computer science Seny Kamara of Brown University has a great blog post called “How Not to Learn Cryptography,” in which he discusses potential strategies for learning cryptography and offers valuable advices. The blog post considers the theoretical aspects of cryptography and, at this point, I’ll quote Bender from Futurama: “I am afraid, we need to use… math.”>
<After “fixing” the gaps in your mathematical background, start reading articles and try to comprehend them, even if they seem over your head at first. Try to develop your interests in one or two particular areas of cryptography, so you can “dig” deeper and deeper. When it comes to learning applied (practical) cryptography, I’ll pass on some advice that I was either given by others or figured out for myself:
• The strongest advice is to read a lot about cryptographic algorithms/suits and their implementation. Focus on real-world algorithms, rather than on “textbook” ones. Familiarize yourself with cryptanalysis techniques and the common pitfalls in implementations. Research the failures of past, for example, the BEAST attack against TLS. And do not forget that security and cryptography go hand-in-hand
• Learn how to use cryptographic tools, libraries, and frameworks.
• Solve crypto challenges and publish your solutions. Working on The Cryptopals Crypto Challenges will provide you with a good learning curve, because you will improve your coding skills (if you need to) and demonstrate attacks on real-world algorithms.
• Implement cryptographic algorithms in the language of your choice. For example, consider the SHA family of hash functions, which is described in FIPS 180-4.
• Create and build your own algorithms just for fun, but do not assume that your algorithms are unbreakable. Try to break your own algorithms and find weaknesses. However, bear in mind this famous saying by Bruce Schneier: “Anyone, from the most clueless amateur to the best cryptographer, can create an algorithm that he himself can’t break.”
• Cryptography Stackexchange is a great place to learn. An excellent way to begin is by asking questions, then move on to providing answers to the questions of others.
• Participate in discussions, including on Peerlyst. Organize educational sessions about topics in cryptography for your peers or co-workers. Participate and contribute to open-source projects.>
Citation information
File:Public key encryption.svg. (2022, October 1). Wikimedia Commons, the free media repository. Retrieved 17:58, February 14, 2023 from https://commons.wikimedia.org/w/index.php?title=File:Public_key_encryption.svg&oldid=693346162.
Shamil Alifov. (2016). How to get started in cryptography (Ch. 5). In Beginner’s Guide To Information Security (pp. 27-31). Peerlyst. Retrieved from https://www.peerlyst.com/posts/peerlyst-announcing-its-first-community-ebook-the-beginner-s-guide-to-information-security-limor-elbaz



